Roaming Computer Settings
Roaming client administrators have access to configure several behavioral options for roaming computers. These options include trusted network, identity, and other general management settings.
Procedure
- Navigate to Deployments > Core Identities > Roaming Computers and click Settings.

- Select a tab and then options on that tab:
General Settings
This tab provides general settings for roaming computers.
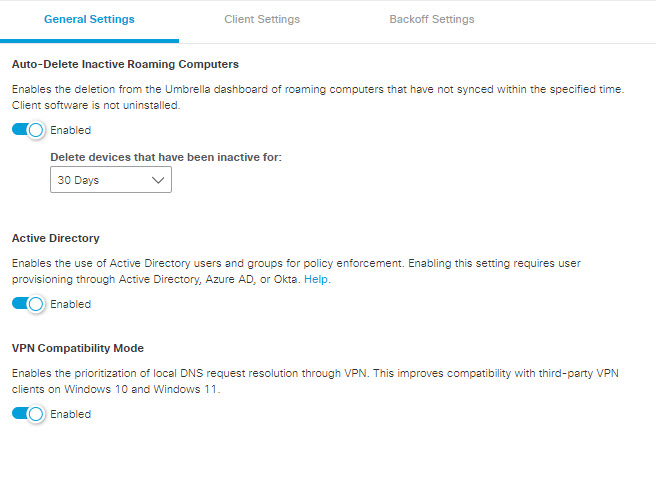
-
Auto-Delete Inactive Roaming Computers—Automatically deletes all roaming computers that have not synced for the specified period of time. Unsynced roaming computers are removed from the Umbrella dashboard, but the client software is not automatically uninstalled from the computer. If a roaming computer comes back online it re-appears in the dashboard once it has re-synced, even if it has been deleted.
-
Active Directory—Enables identity support for roaming computers. Identity support is an enhancement to the Umbrella roaming client or the Cisco Secure Client Umbrella roaming security module that provides Active Directory user and group identity-based policies, in addition to user and private LAN IP reporting. See Identity Support for the Roaming Client.
-
VPN Compatibility Mode—The Cisco Umbrella roaming client works with most VPN software; however, certain Cisco Secure Roaming security module and other VPN profiles may not resolve local DNS correctly on a VPN connection with Windows 10 due to the elimination of the system DNS binding order. The local LAN may bind above the VPN, failing to resolve local DNS over the tunnel. Select this setting to apply the legacy binding order behavior. For more information, see VPNs (including Cisco Secure Client) + Standalone Roaming Client + Windows 10 and 11: DNS Binding Order VPN compatibility mode.
Client Settings
This tab presents settings specific to Cisco Secure Client and Umbrella Roaming Client.
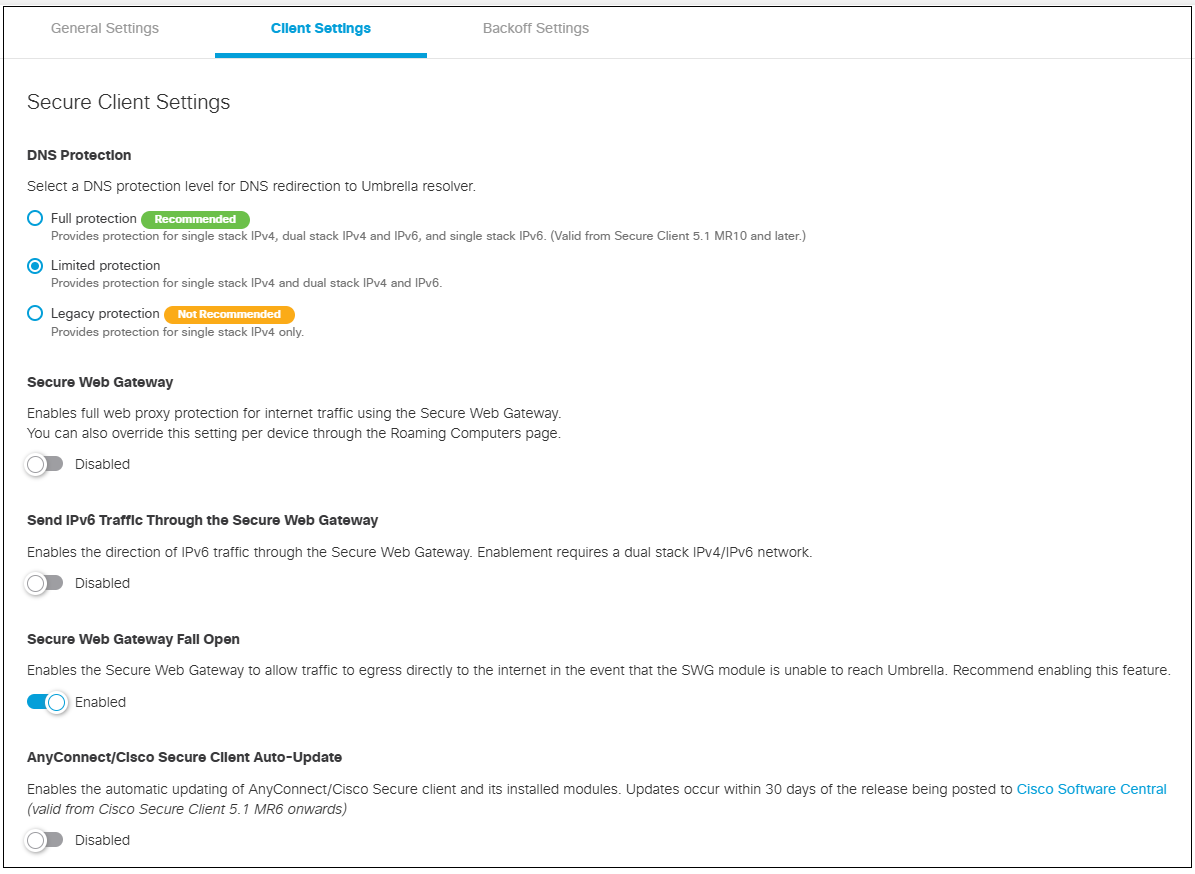
Secure Client Settings
- DNS Protection
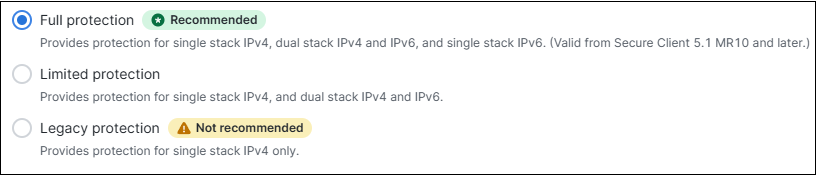
Choose one of the following options to provide DNS protection:
- Full Protection: Provides protection for single stack IPv4 network, dual stack IPv4 and IPv6 network, and single stack IPv6 network.
- Limited Protection: Provides protection for single stack IPv4 network, and dual stack IPv4 and IPv6 network.
- Legacy Protection: Provides protection for single stack IPv4 network only.
The previous dashboard configuration for IPv6 DNS protection allowed enabling protection over IPv6.
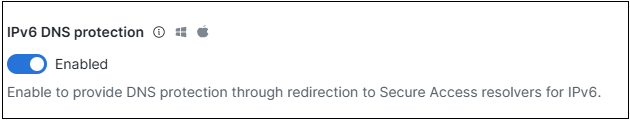
This earlier configuration is now replaced with the new DNS protection options described above.
- If the earlier IPv6 DNS protection configuration was disabled, the new configuration defaults to Legacy Protection.
- If the earlier IPv6 DNS protection configuration was enabled, the new configuration defaults to Limited Protection.
Note : For optimal security, we recommend using the Full Protection configuration, available in Cisco Secure Client 5.1.10.233 (MR 10) or later.
-
Secure Web Gateway— Enables full web proxy protection for internet traffic using the Secure Web Gateway. This is the SWG global setting for roaming devices.
a. To override the global setting for a specific device, select the device, then click the ellipsis (...) at top right.
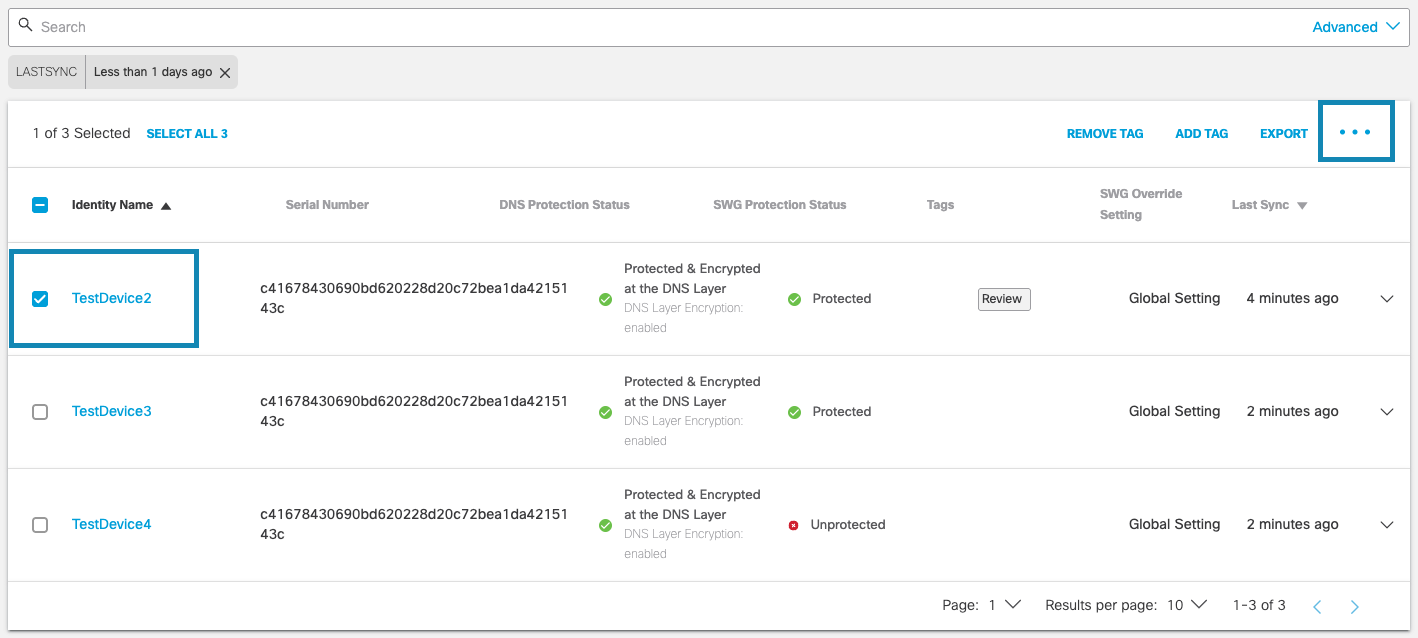
b. Choose to delete the identity associated with the device, enable or disable the SWG Agent, or follow global settings.
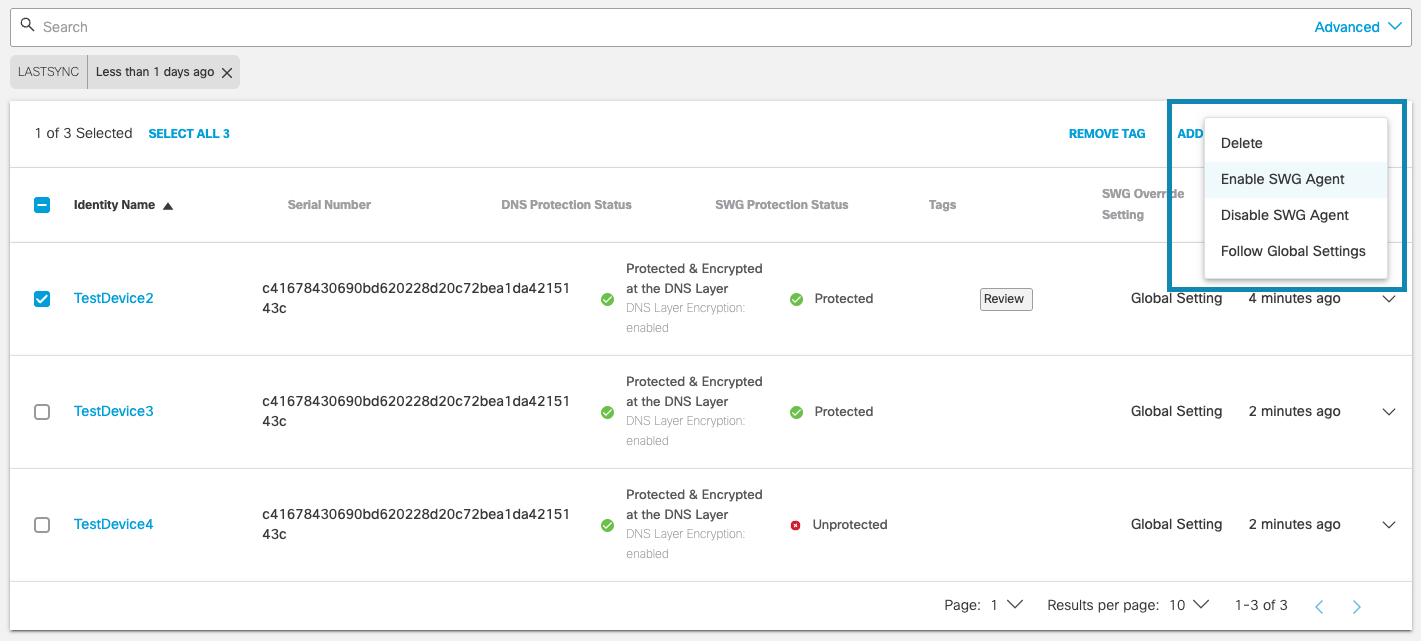
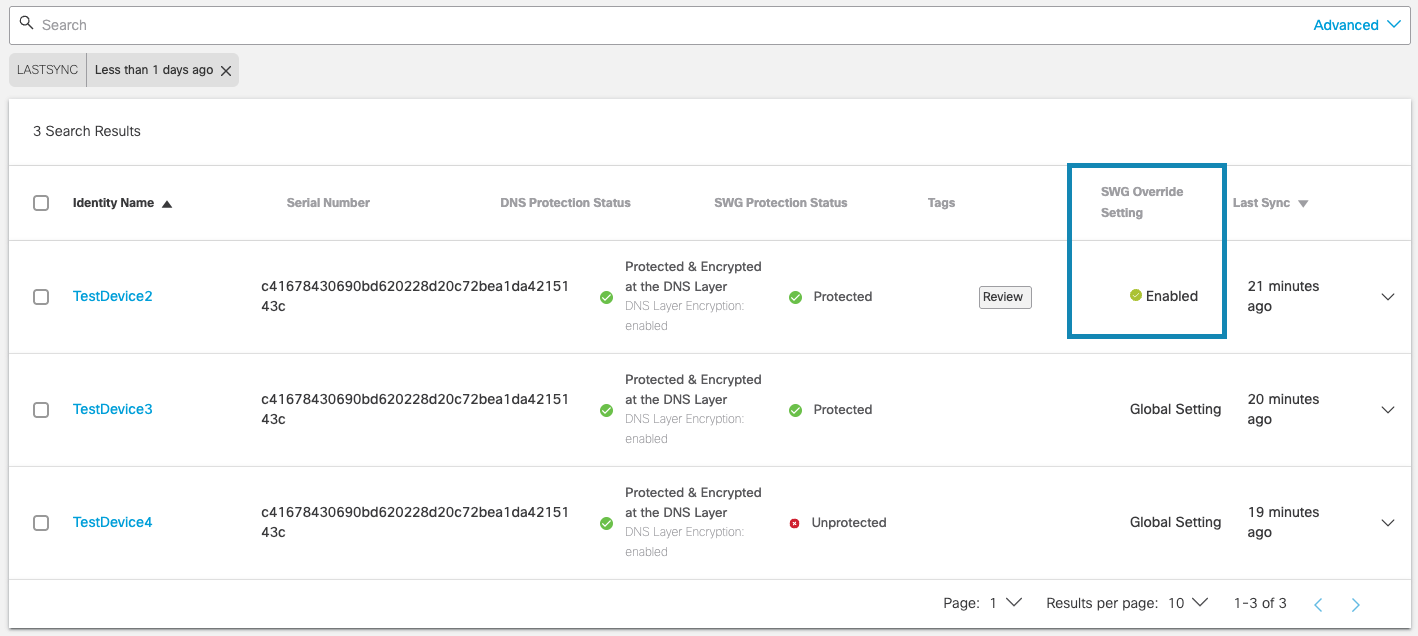
c. Your choice will update the SWG Override Setting value for the device.
- Send IPv6 Traffic Through the Secure Web Gateway— When enabled, IPv6 traffic is directed to SWG. When disabled, IPv6 traffic goes directly to the internet.
Note: Enabling this requires a dual stack IPv4/IPv6 network. - Secure Web Gateway Fail Open — When enabled, SWG allows traffic to egress directly to the internet when the SWG module is unable to reach Umbrella. When disabled, the internet is not accessible when the SWG module is unable to reach Umbrella (this is not recommended).
- AnyConnect/Cisco Secure Client Auto-Update— When enabled, the AnyConnect or Cisco Secure Client and all of its installed modules will automatically update within 30 days of a release being posted to Cisco.com. For more information, see the Future of auto-update for Umbrella customers. Customers who have upgraded to at least Cisco Secure Client 5.1.6 (MR6) will be able to auto-update to newer versions if auto-update has been configured in the dashboard.
Umbrella Roaming Client Settings
- IPv6 DNS Protection— Provides DNS protection through redirection to Umbrella resolvers for IPv6.
Note: DNS protection over IPv6 DNS64 support is not available.
Backoff Settings
This tab presents settings to enable the client to backoff from providing DNS and Secure Web Gateway protection in certain scenarios.
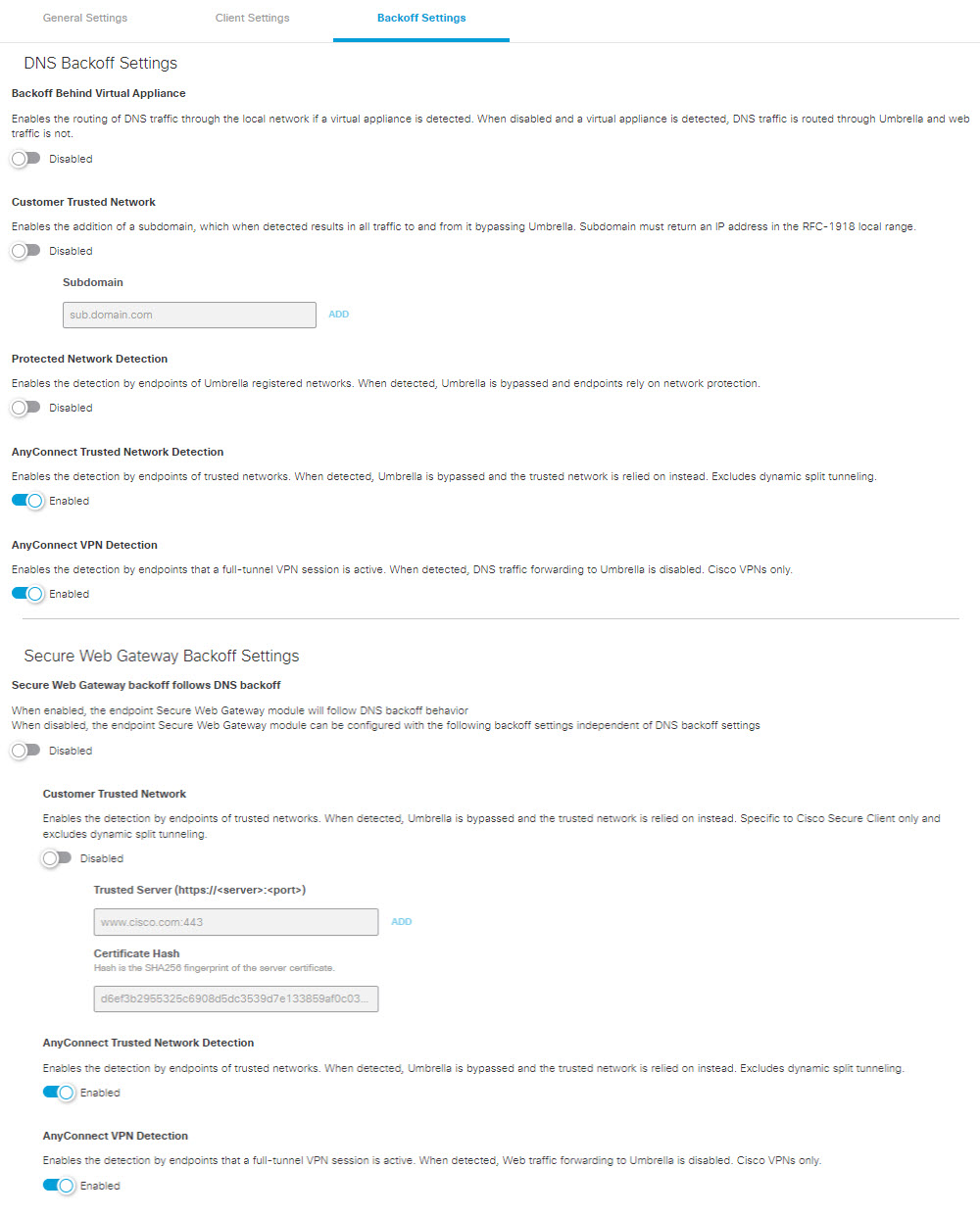
DNS Backoff Settings
- Backoff Behind Virtual Appliance— When this setting is enabled and the client detects a virtual appliance, DNS traffic goes through the local network. When this setting is disabled and the client detects a virtual appliance, DNS traffic is redirected to Umbrella, while web traffic is not.
Note: This setting also applies to the iOS setting on the Mobile Device page. - Customer Trusted Network — When enabled, DNS and web redirection to Umbrella is disabled if the specified subdomain name is found on the network and resolves to an RFC-1918 local IP address (e.g. "10.0.0.1").
- Protected Network Detection— Disables the DNS-based protection applied by the Cisco Secure Client Umbrella module while on a network protected by Umbrella. This includes the intelligent proxy as it is a DNS-based redirect. Relies on the protection of the network for all features. To trigger this setting, network registration and the network must be the higher policy (not same, but higher) and the local DNS server egress network must be the same network registration as straight out from the computer to 208.67.222.222. Having the network in the same organization will not trigger the disabling of traffic redirection.
- AnyConnect Trusted Network Detection— Trusted Network Detection (TND) is configured in the Cisco Secure Client's AnyConnect VPN profile. Enabling this setting disables DNS traffic forwarding to Umbrella whenever TND indicates the current network is trusted.
- AnyConnect VPN Detection— When enabled, DNS traffic forwarding to Umbrella is disabled when the endpoint detects that a full-tunnel VPN session is active. This is specific to Cisco VPNs.
Note: For tunnels, this functionality is supported only for full tunnels. It does not work for full tunnels with dynamic split tunneling.
Secure Web Gateway Backoff Settings
- Secure Web Gateway backoff follows DNS backoff— When enabled, the endpoint Secure Web Gateway module follows DNS backoff behavior when DNS backs off for any of the following DNS backoff settings: Customer Trusted Network, AnyConnect Trusted Network Detection, or AnyConnect VPN Detection.
Note: The SWG module will not follow DNS backoff for the following DNS backoff settings: Backoff Behind Virtual Appliance, or Protected Network Detection.
When disabled, the endpoint Secure Web Gateway module can be configured with the following backoff settings independent of DNS backoff settings:
Note: The following backoff settings require upgrade to Cisco Secure Client Version 5.1.3.62.
- Customer Trusted Network— When enabled, the endpoint attempts to detect customer trusted networks specified with the Trusted Server and Certificate Hash fields. When such networks are detected, Umbrella is bypassed and endpoints rely on network protection. This setting is independent of DNS backoff.
- AnyConnect Trusted Network Detection— Trusted Network Detection (TND) is configured in the Cisco Secure Roaming security module VPN Client profile. Enabling this setting disables web traffic forwarding to Umbrella whenever TND indicates the current network is trusted.
- AnyConnect VPN Detection— When enabled, web traffic forwarding to Umbrella is disabled when the endpoint detects that a full-tunnel VPN session is active. This is specific to Cisco VPNs.
Configure Protected Networks for Roaming Computers< Roaming Computer Settings
Updated 5 months ago
