Threat Type Details
The Threat Types Details provides information about specific threat types that your environment may have been exposed to. You can explore the most active identities, identity types, destinations, and threats associated with this threat type.
Table of Contents
- Prerequisites
- View a Threat's Details
- View a Threat Type's Requests
- View the Threat Type's Impact on Your Environment
- View More Details in Activity Search
Prerequisites
- A minimum of Read Only access to the Umbrella dashboard. See Manage User Roles.
View a Threat's Details
- Navigate to Reporting > Core Reports > Top Threats.
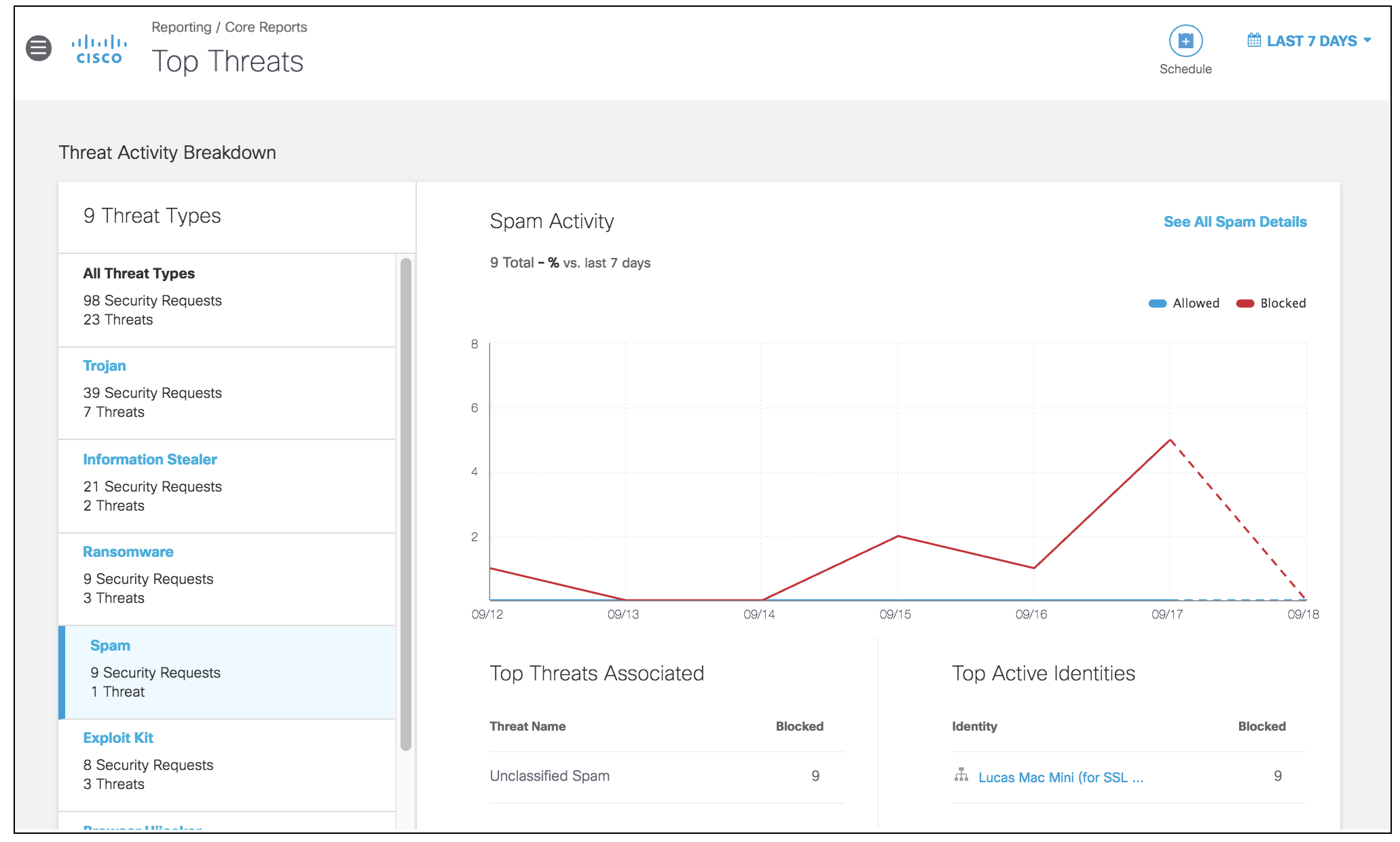
- Choose a threat type and click the name to view further details.
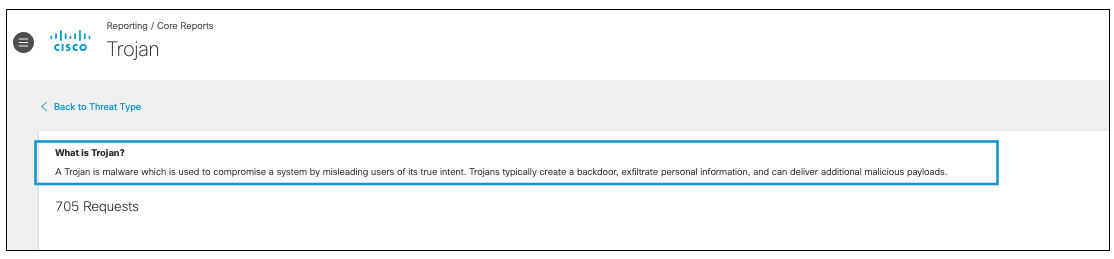
- View the threat type definition.
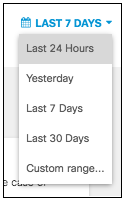
- Select a time frame to view the results of the report.
You can select results for the last 24 hours, the previous day (yesterday), the last week, the last 30 days, or a custom range within the last 30 days.
View a Threat Type's Requests
The first graph on the details page depicts the requests for the threat type within the selected time period. A detailed description of the threat type provides insight as to what type of exposure the requests pose to your environment. A request is any time an identity makes a request to access a destination, and a threat is when this request is deemed malicious.
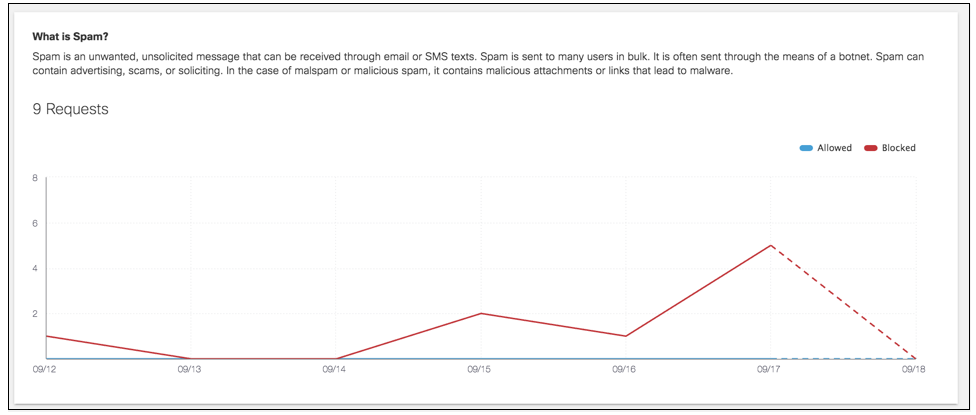
- Navigate to Reporting > Core Reports > Top Threats.
- Choose a threat type and click the name to view further details.
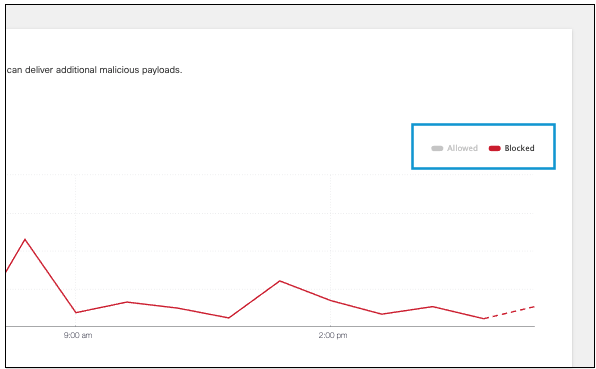
- Choose to view all requests, only Blocked requests, or only Allowed requests. By default, both allowed and blocked are shown. Click either name to hide those requests in the graph.
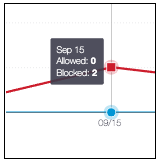
- Hover on a point in the graph to reveal the date and time and the number of Blocked and Allowed requests at that point.
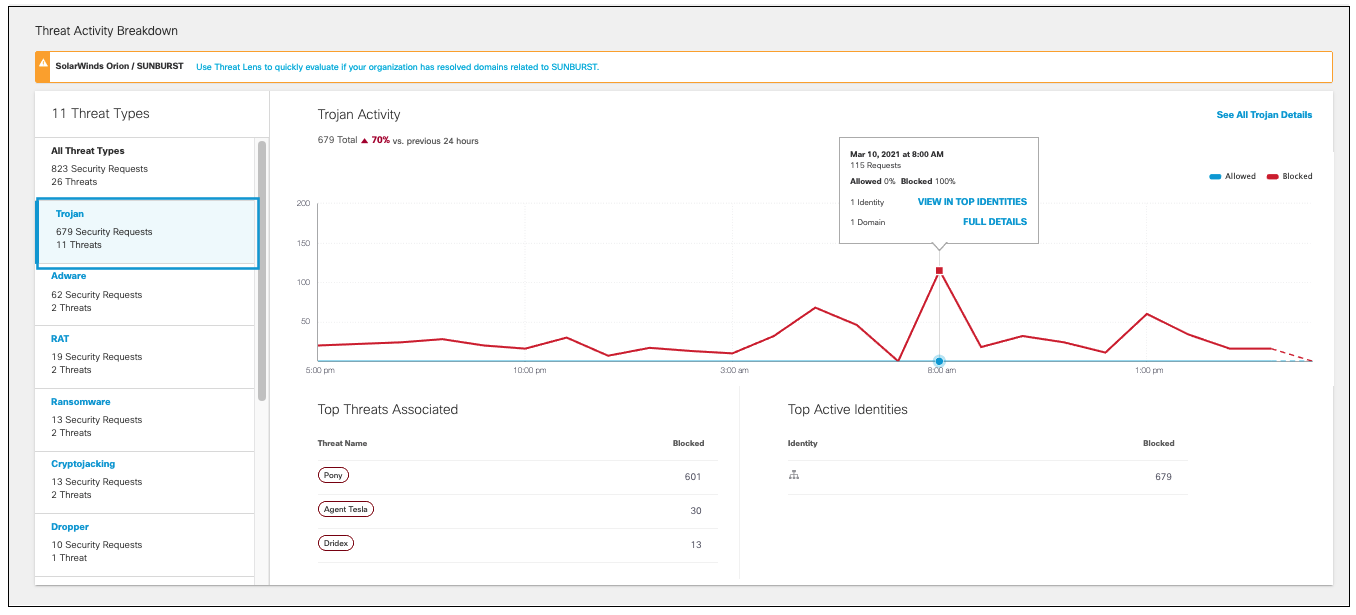
View the Threat Type's Impact on Your Environment
- Navigate to Reporting > Core Reports > Top Threats.
- Choose a threat type and click the name to view further details.
- View the most active identity types.
The most active identity types lists the types of identities most actively making requests and whether those requests were blocked or allowed.
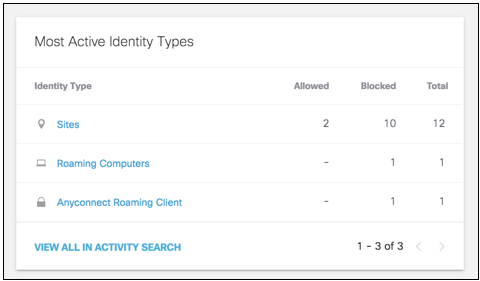
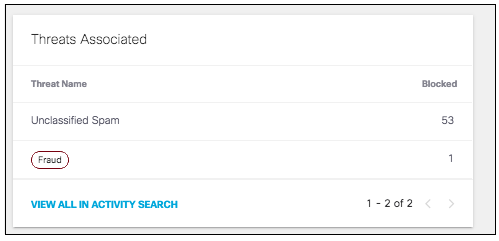
- View the threats associated with this threat type and the number of threats blocked.
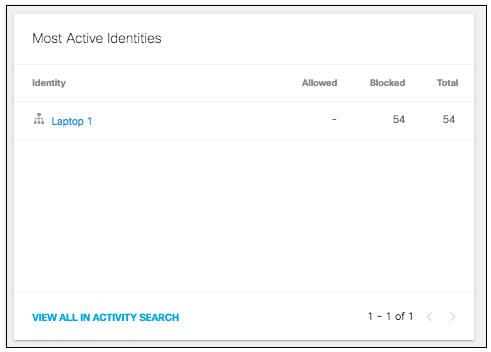
- View the most active identities associated with this threat type and how many requests were allowed or blocked.
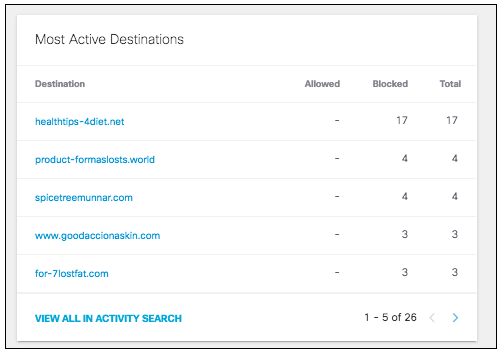
- View the most active destinations where this threat type has been most associated during requests. The list provides the total number of requests during the given time period for each destination and how many were blocked or allowed.
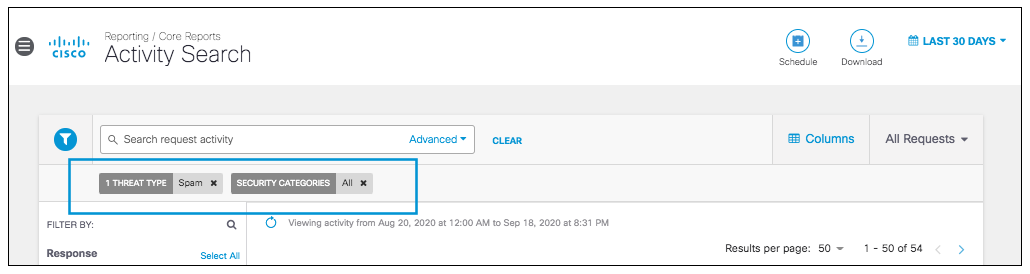
View More Details in Activity Search
Clicking on an individual identity type, identity name, destination, or clicking View All in Activity Search will redirect you to the Activity Search filtered by the appropriate fields.
Top Threats Report < Threat Type Details > Threat Type Definitions
Updated almost 2 years ago
