App Discovery Report
Monitor the cloud apps in use by your organization with the App Discovery report. To effectively reduce the risk introduced by apps, a good approach is to look for a reduction over time in the number of DNS requests made by apps with high and very high-risk assessments. You can monitor this with the App Discovery report.
From the App Discovery report you can also assign values of your choosing to app review status labels and app risk scores. (See Change App Details).
You can configure your policies to block many apps when risk levels are unacceptable and/or an app category is inappropriate for your organization. For more information, see Control Apps.
New Data
App Discovery data is aggregated and processed once a day so it may take up to 24 hours for new data to populate in the report. Logging of traffic is required for App Discovery to function.
Prerequisites
- A minimum of Read Only access to the Umbrella dashboard. See Manage User Roles.
View the Dashboard
- Navigate to Reporting > Core Reports > App Discovery.

- View the discovered apps in your environment by review status label.
- Unreviewed—The app has not yet been assigned any label.
- Under Audit—The app is currently being reviewed.
- Not Approved—The app should not be approved for use in your environment.
- Approved—The app may be used in your environment.

Note: Once an app has been given a label, it cannot be set back to Unreviewed. You can use the Under Audit label for apps that still need review. When you set an app to Not Approved, it is not automatically blocked from use. Labels within the App Discovery report are used to help review apps in your environment. You must configure application settings within a policy to block apps. For more information, see Control Apps.
- View the flagged categories.
Cisco's Cloud Security researchers categorize apps according to function, source, and other factors. The categories of most interest (and most risk) are:
- Anonymizers—Services that provide an anonymous proxy tool that attempts to make activity on the Internet untraceable. Apps in this category can introduce data exfiltration risks.
- Cloud Storage—Applications that offer massively scalable storage capacity that can be used for applications, and file storage. Apps in this category can also be used for data exfiltration.
- Collaboration—Applications that may store sensitive data in unreliable services or unsecured environments.
- Games—Online and mobile games. While games are not notable for data exfiltration risks, some can be used as attractive ways to introduce malware.
- Generative AI—Applications that have the potential to generate misleading or fraudulent content and copyright or intellectual property infringements.
- Media—Applications that can contribute to productivity loss and are frequently managed as unwanted bandwidth consumers.
- P2P—Peer to Peer torrents like apps and protocols. These apps can be used for data exfiltration.
- Social Networking—Can be used to transmit sensitive data as well as contribute to productivity loss.
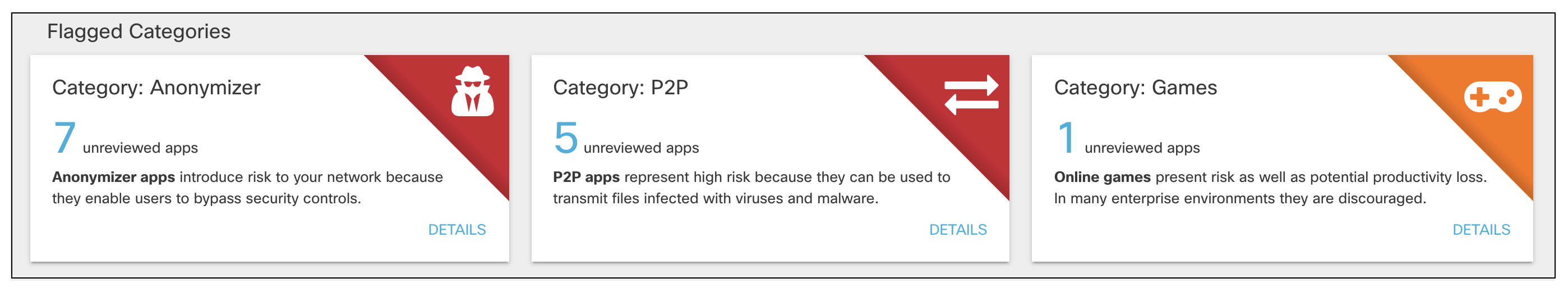
For a complete list of application categories, see Application Categories.
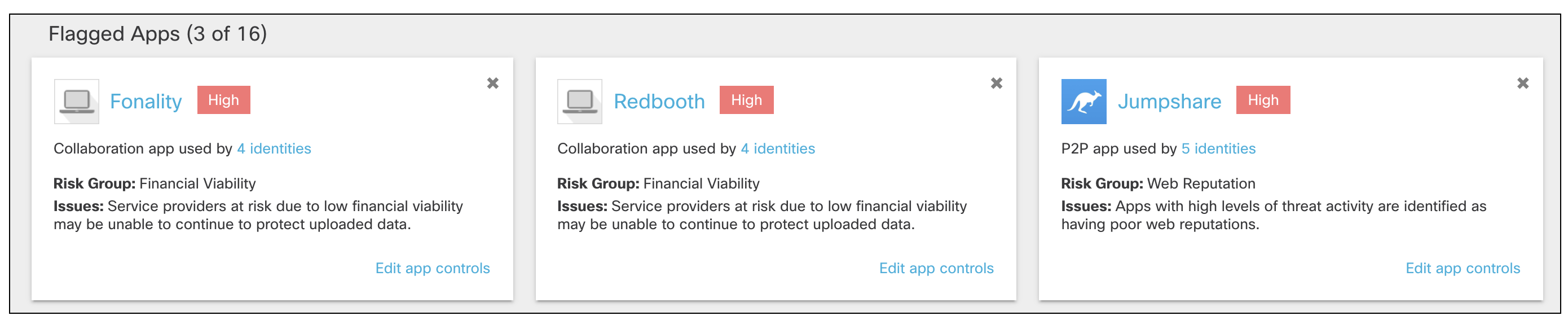
- View the flagged apps.
These apps are flagged based on their risk group, different from the categories.
Note: Dismissing a flagged app card hides it from the overview. It does not label or block the app.
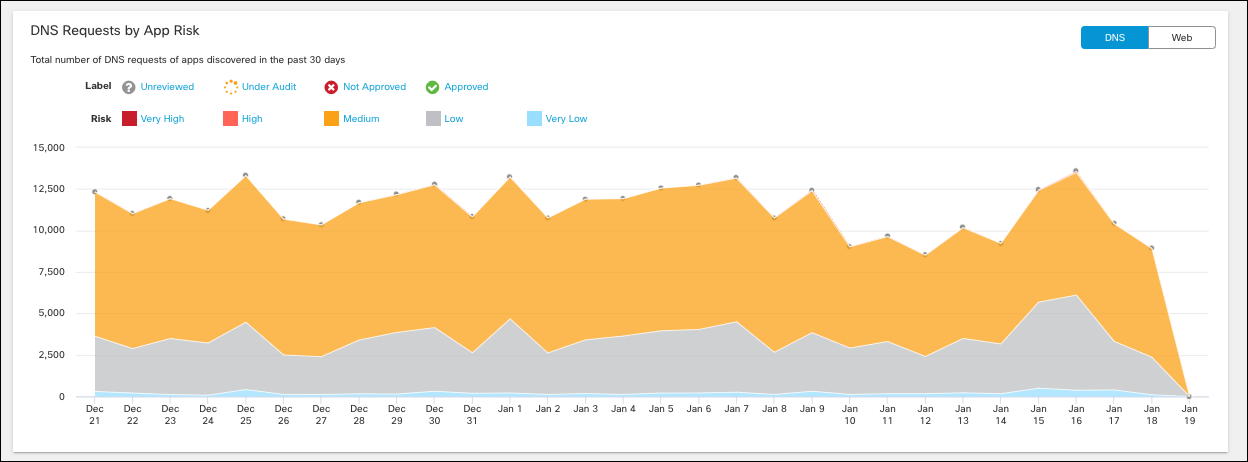
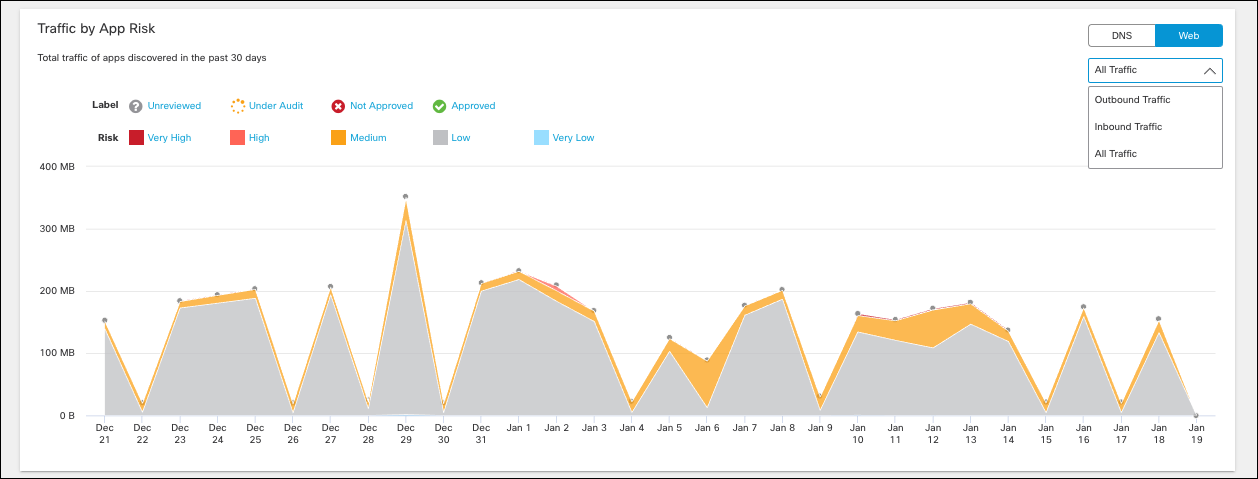
- View DNS requests and traffic by App Risk.
The graph shows the total number of DNS requests for apps discovered in the past 30 days. Umbrella assigns a risk score to apps based on several factors. The DNS requests made by a high-risk app can be considered more problematic than the same number of requests made by an app with a lower risk score.
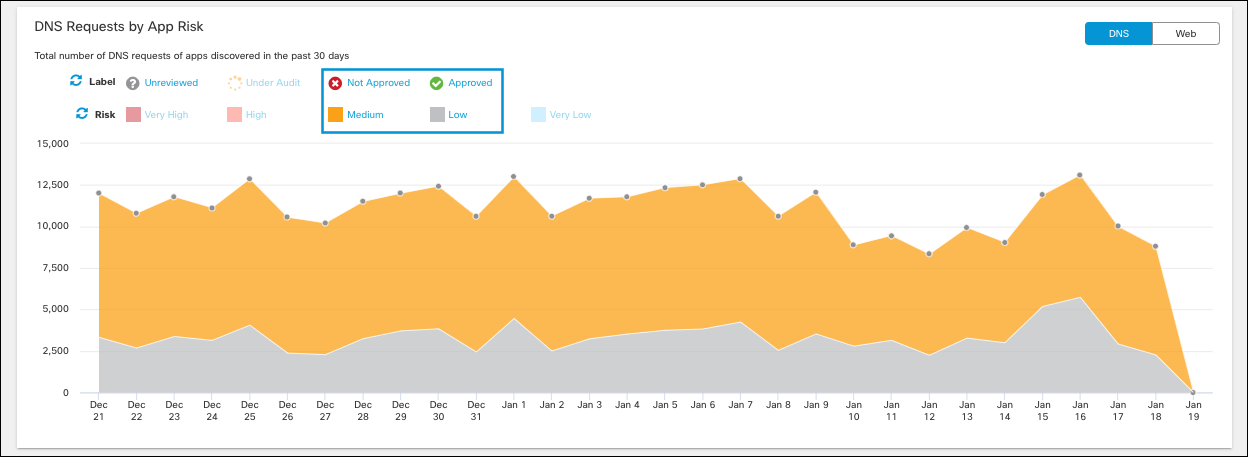
a. Filter the graph by label and risk.
b. Review Traffic (bytes in and out) by App Risk for the last 30 days.

c. View All Traffic, Outbound Traffic or Inbound Traffic.
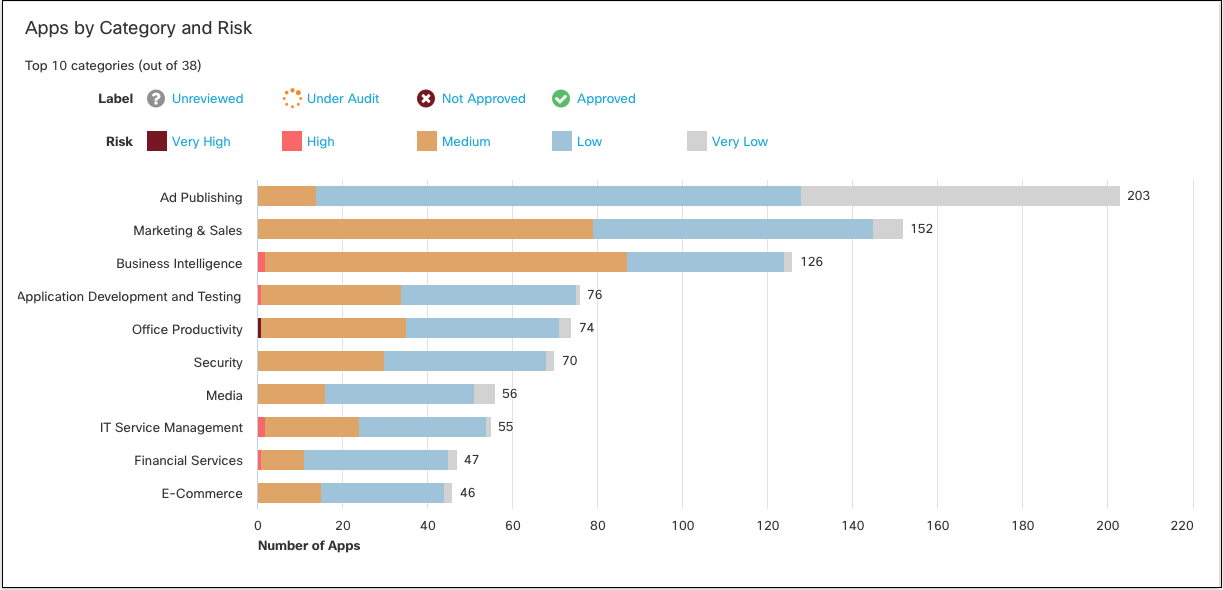
- View apps by category and risk.
Click a bar on the chart to view apps in that category in the App Grid.
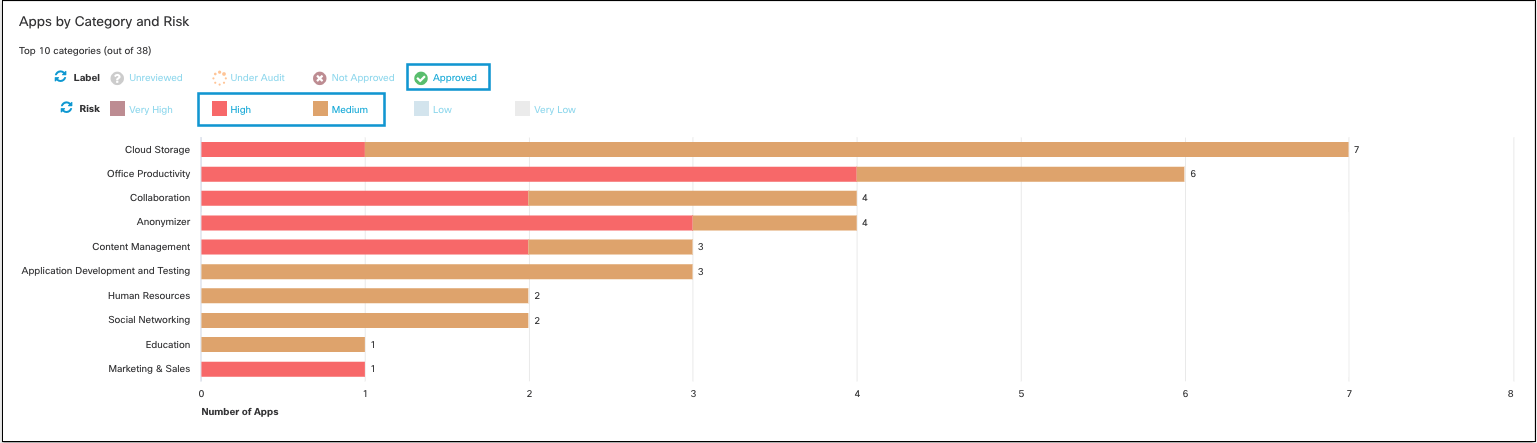
a. Filter by label and risk.
Use Search and Advanced Search < App Discovery Report > View the Highest Risk Apps
Updated 11 months ago
