Configure Tunnels with Cisco ISR
Table of Contents
Prerequisites
The following prerequisites must be met for the tunnel to work successfully.
Licensing and Hardware
- A valid Cisco Umbrella SIG Essentials or SIG Add-On subscription or a free SIG trial.
- A router (ISR-G2, ISR4K or CSR) with a security K9 license to establish an IPsec tunnel.
Note: A HSEC license will be required to get high-throughput internet bandwidth for SLVPN tunnel setup.
Network Access
- You must select an Umbrella SIG Data Center IP address to use when creating the IPsec tunnel.
In the sample commands, <umbrella_dc_ip> refers to this IP address. We recommend choosing the IP address based on the data center located closest to your device.
The following ports must be open before connecting to the tunnel:
- UDP ports 500 and 4500.
Cisco router (ISR-G2, ISR4K or CSR) devices do not require public static IPv4 address(es) configured on the interface that will connect to the public internet and Cisco Umbrella SIG service. They can be behind a NAT device. This is because we can specify a text as its IKE ID. This ID in combination with the PSK is used to successfully authenticate the Cisco router (ISR-G2, ISR4K or CSR) devices with the Cisco Umbrella SIG service.
Text as an IKE ID also allows for multiple tunnels to be established from the same Cisco router device with a single IP address. This provides an opportunity to increase bandwidth by increasing the number of tunnels.
Configure Tunnels in Umbrella
- Navigate to Deployments > Core Identities > Network Tunnels, then click Add.
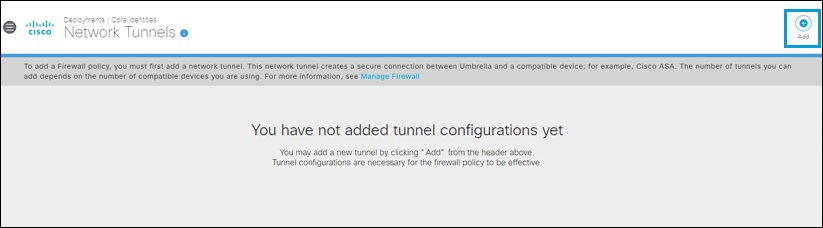
- Give your tunnel a meaningful Tunnel Name, from the Device Type drop-down list choose ISR, and then click Save.
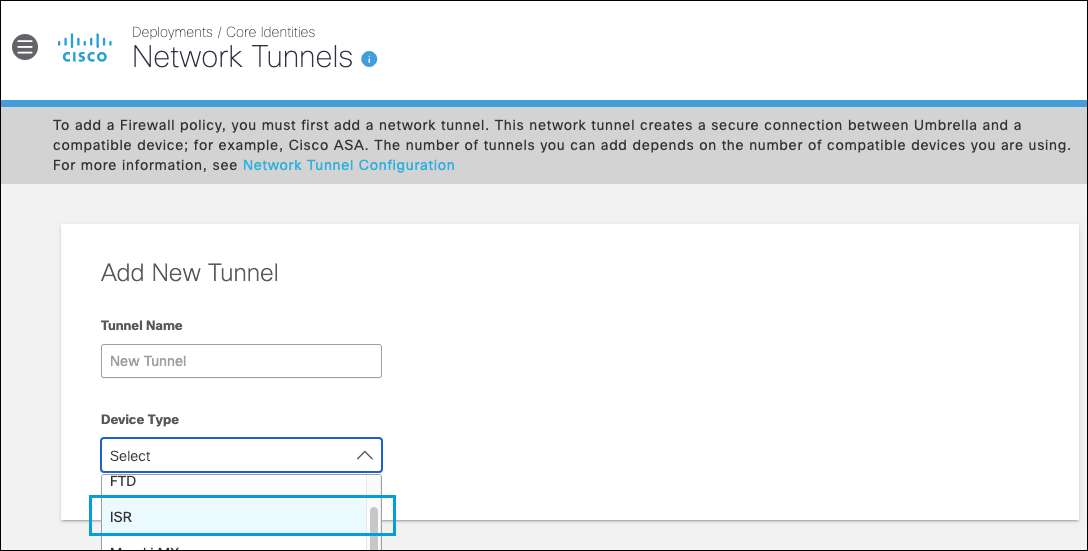
- Select your Tunnel ID from the drop-down list. Enter the Pre-Shared-Key (PSK) Passphrase.
- Choose an appropriate site from the Associate Tunnel with Site drop-down list and optionally, enter an IP address to the IP Address Ranges field which you would like to send to Umbrella SIG.
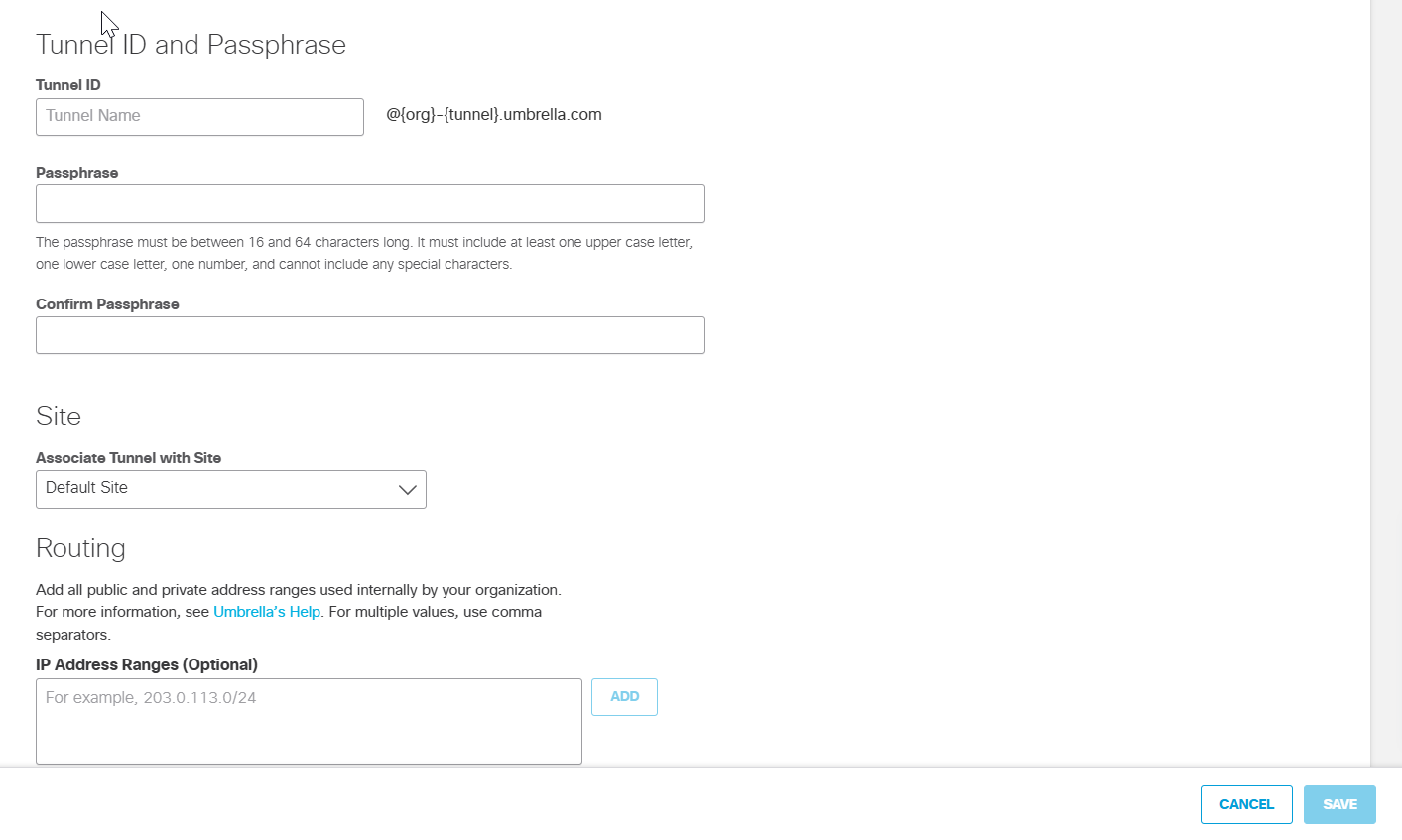
- Click Save and then copy the Tunnel ID and Passphrase.
The new tunnel appears in the Umbrella dashboard with a status of Not Established. The tunnel status is updated once it is fully configured and connected with the ISR.
Configure ISR (G2, 4K) or CSR
Follow these steps to connect the Cisco router to the Cisco Umbrella Cloud-Delivered Firewall.
- Configure the IKEv2 proposal.
ISR routers support a default proposal and policy for IKEv2, with a predefined encryption, integrity and DH group. These values change across different software versions. You can either use the default proposal or you can create your own proposal. Your proposal needs to be attached to the policy with matching parameters. Create an IKEv2 keyring profile and configure the peer address and pre-shared key, associate the keyring profile to the IKEv2 profile, set the local identity as email and configure the IKE ID (email) which you get from the Tunnel Configuration dashboard.
For example, the default IKE proposal of an ISR running 16.11.01a:
ISR-4221#sh ver
Cisco IOS XE Software, Version 16.11.01a
ISR-4221#show crypto ikev2 proposal umbrella-prop
IKEv2 proposal: umbrella-prop
Encryption : AES-GCM-256
Integrity : none
PRF : SHA256
DH Group : DH_GROUP_256_ECP/Group 19 DH_GROUP_384_ECP/Group 20
- Define the IKEv2 Keyring and IKEv2 profile.
Create your IKEv2 keyring and IKEv2 profile with the [umbrella_dc_ip] of the Umbrella Data Center closest to your location. Then associate the IKEv2 keyring to the IKEv2 profile.
Replace [Portal_Tunnel_ID] and [Portal_Tunnel_Passphrase] with the Tunnel ID and Passphrase you configured in section Configure Tunnels in Umbrella.
crypto ikev2 keyring umbrella-kr
peer umbrella
address [umbrella_dc_ip]
pre-shared-key [umbrella-tunnel-psk]
!
crypto ikev2 profile umbrella-profile
match identity remote address 146.112.0.0
255.255.0.0
identity local email [ummbrella-email]
authentication remote pre-share
authentication local pre-share
keyring local umbrella-kr
dpd 10 3 periodic
!
- Define the IPSec transform-set, profile, and policy.
Create the transform-set and IPsec profile. Then associate the transform-set and IKEv2 Profile with the IPSec profile. Refer to Supported IPsec Parameters for the recommended algorithms.
crypto ipsec transform-set umbrella-ts esp-gcm 256
mode tunnel
crypto ipsec profile umbrella
set transform-set umbrella-ts
set ikev2-profile umbrella-profile
crypto ikev2 policy umbrella
match address local [Router_WAN_IP]
proposal umbrella-proposal
- Create the tunnel interface.
Define the static tunnel interface with the peer IP as the Umbrella VPN headend IP and associate the IPsec profile under the tunnel. Make sure the tunnel interface does not contain NAT related commands; traffic sent to Umbrella should not have NAT applied.
interface Tunnel1
ip unnumbered [interface-name]
ip tcp adjust-mss 1280
tunnel source [interface-name]
tunnel mode ipsec ipv4
tunnel destination [umbrella_dc_ip]
tunnel protection ipsec profile umbrella
- Configure routing rules.
Define the traffic which needs to be tunneled to the CDFW. Based on the requirements, these ACL rules can be modified.
The route-map needs to be associated with the LAN interface of the router where the device receives the traffic.
In the following examples, 192.168.20.0/24 is the LAN subnet, and GigabitEthernet is the LAN interface.
ip access-list extended traffic-to-umbrella
permit ip [lan-ip] any
!
route-map umbrella-route-map permit 10
match ip address traffic-to-umbrella
set interface Tunnel1
!
interface GigabitEthernet [lan-interface-name]
ip policy route-map umbrella-route-map
Test Your Configuration
Check Tunnel Status
Use the following command to verify the tunnel status on your ISR.
show crypto session detail and the output must show the tunnel status as UP-ACTIVE.
Substitute the IP address of the Umbrella data center nearest your location for [umbrella_dc_ip].
ISR#show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect, U - IKE Dynamic Route Update
Interface: Tunnel1
Profile: umbrella
Uptime: 14:53:47
Session status: UP-ACTIVE
Peer: [umbrella_dc_ip] port 4500 fvrf: (none) ivrf: (none)
Phase1_id: [umbrella_dc_ip]
Desc: (none)
Session ID: 1
IKEv2 SA: local 10.10.10.201/4500 remote [umbrella_dc_ip]/4500 Active
Capabilities:DFNXU connid:4 lifetime:09:06:13
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 0 drop 0 life (KB/Sec) 4608000/2499
Outbound: #pkts enc'ed 0 drop 0 life (KB/Sec) 4608000/2499
Manually Trigger the Tunnel
Should the tunnel not come up immediately, or should it need to be manually triggered for any reason, select the tunnel interface, and issue the shutdown and no shutdown commands.
ISR(config)#int T1
ISR(config-if)#shutdown
ISR(config-if)#no shutdown
Verify Tunnel Status
Verify the tunnel status with show crypto session remote <Headend IP> detail. See the example output.
ISR#show crypto session remote 146.112.66.2 detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect, U - IKE Dynamic Route Update
S - SIP VPN
Interface: Tunnel1
Profile: Umbrella
Uptime: 00:39:11
Session status: UP-ACTIVE
Peer: 192.0.2.0 port 4500 fvrf: (none) ivrf: (none)
Phase1_id: 192.0.2.0
Desc: (none)
Session ID: 1
IKEv2 SA: local 192.0.2.0/4500 remote 146.112.66.2/4500 Active
Capabilities:DN connid:3 lifetime:23:20:49
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 0 drop 0 life (KB/Sec) 4607996/1248
Outbound: #pkts enc'ed 0 drop 0 life (KB/Sec) 4607997/1248
Configure Tunnels with Cisco Adaptive Security Appliance (ASA) < Configure Tunnels with Cisco ISR > Configure IKEv2 IPsec Tunnel with Umbrella
Updated about 1 month ago
