Configure Tunnels with Cisco Router in AWS
The Amazon Web Services (AWS) Site-to-Site VPN is not compatible with Cisco Umbrella’s IPsec headend. An initial connection will succeed but it will not maintain connectivity. As an alternative, the information here provides an alternative option to setup IPSec tunnels between AWS Virtual Private Clouds (VPCs) and Umbrella to protect workload traffics. This document covers two types of AWS deployment:
- Multiple isolated AWS VPCs: with each VPCs having their own internet access.
- Multiple interconnected AWS VPCs: with interconnectivity through the AWS Transit Gateway.
Note: This document assumes that the reader has sufficient familiarity with the AWS dashboards and different AWS components.
Table of Contents
Multiple Isolated AWS VPCs
In this setup, a customer will have multiple VPCs running in isolation and no interconnectivity between the VPCs. Each VPCs has their own internet gateway configured for access to the outside.
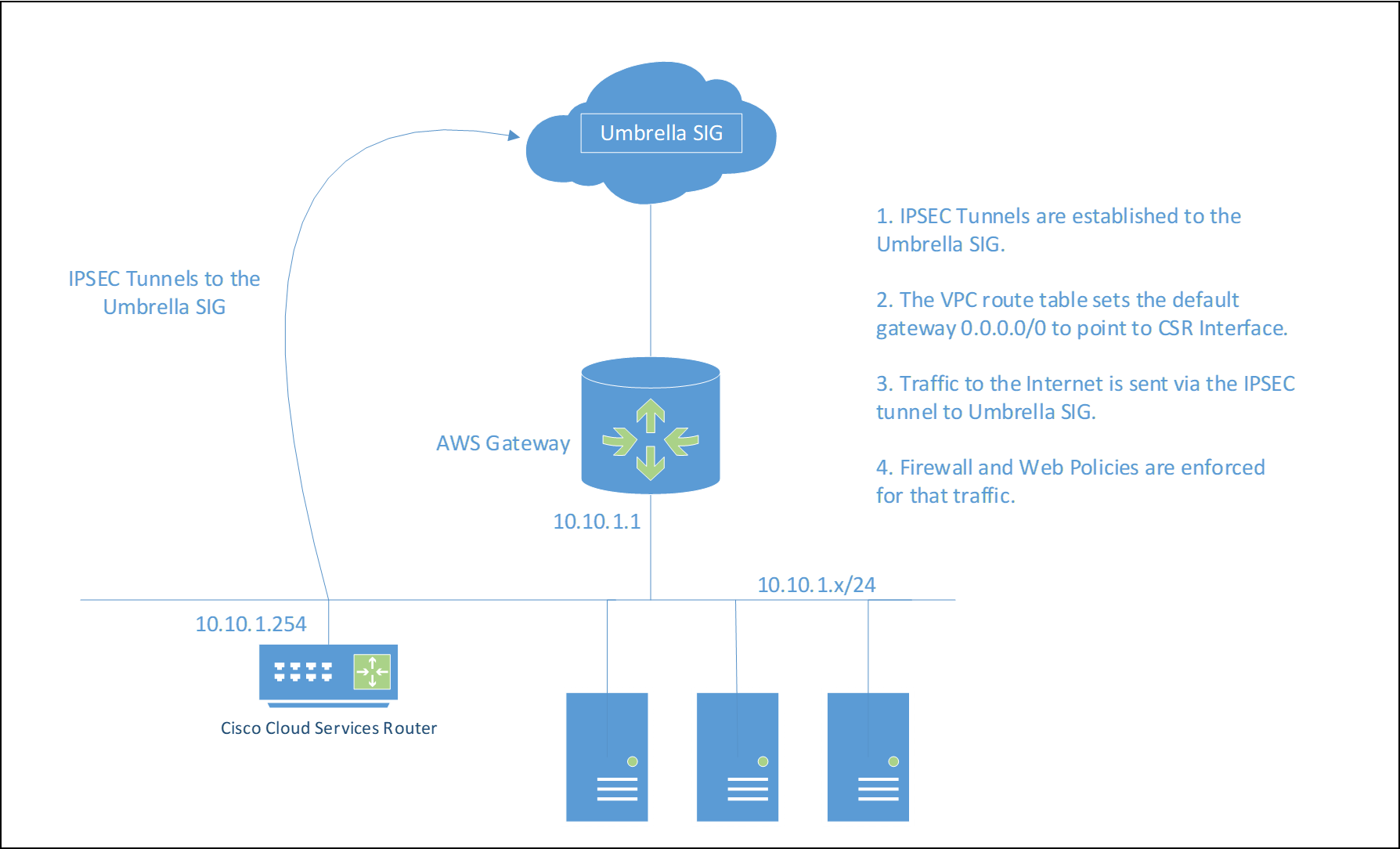
Each VPC has its own CSR and multiple subnets can be supported within a VPC via a private subnet.
Set up the VPC with a Cloud Services Router (CSR)
- From the AWS dashboard, search for VPC, then Virtual Private Cloud > Your VPCs > Create VPC.
- Set the VPC Name Tag to
SIG-VPC1. - In IPv4 CIDR block, set the subnet range to 10.10.1.0/24.
| VPC Name Tag | IPv4 CIDR | Tenancy |
|---|---|---|
| SIG-VPC1 | 10.10.1.0/24 | Default |
- Create one subnet in the VPC (Virtual Private Cloud > Subnets > Create subnet).
| Subnet Name Tag | VPC | IPv4 CIDR |
|---|---|---|
| vpc1-10.10.1.0 | SIG VPC | 10.10.1.0/24 |
Note: The AWS VPC subnets are not a true layer-3 network and there is no advantage to multiple subnets for this use case. The Cisco CSR will be a router-on-a-stick.
- Navigate to Virtual Private Cloud > Internet Gateways > Create Internet gateway to create an Internet Gateway and attach it to the SIG-VPC1.
- Navigate to Virtual Private Cloud > Route Tables > Create route table and create a new Route Tables for SIG-VPC1.
The Umbrella IPsec head-end IP addresses being used must explicitly use the Internet Gateway vpc1-10-10-1-0-igw. Assign the Name Tag asSIG-VPC1-RT.
Only the IPsec head-ends that are being used need to be defined in the route table.
The default gateway will use the Internet Gateway vpc1-10-10-1-0-igw. The example route table is rtb-08e80b1fddd2c09f5 and will be references later.
Note: Once the CSR is configured, the VPC default route changes to point to the CSR Network Interface.

- Add an additional host route for any Internet hosts that need to access this VPC through the Internet Gateway.
Deploy and Configure the Cisco CSR Instance
Deploy the Cisco CSR 1000V to tunnel traffic from private subnets to Umbrella.
- Search for the Cisco CSR image in AWS Marketplace and deploy as follows:
Instance Attribute Field Value AMI As per customer requirement Instance Type As per customer requirement Network 10.10.1.0/24 Subnet vpc1-10.10.1.0 Auto-assign Public IP Yes. This is required to establish IPSE tunnels to the SIG head-ends. Network Interfaces Primary IP: 10.10.1.254
Assign the Name Tag as VPC1-CSR. This is for reference as a label only.
2. Once deployed, the Cisco CSR instance has a single interface. This configuration is a router-on-a-stick.
3. From the Actions menu, clear Enable.
Once the EC2 CSR has been created, the source/destination check must be disabled for the Cisco CSR.
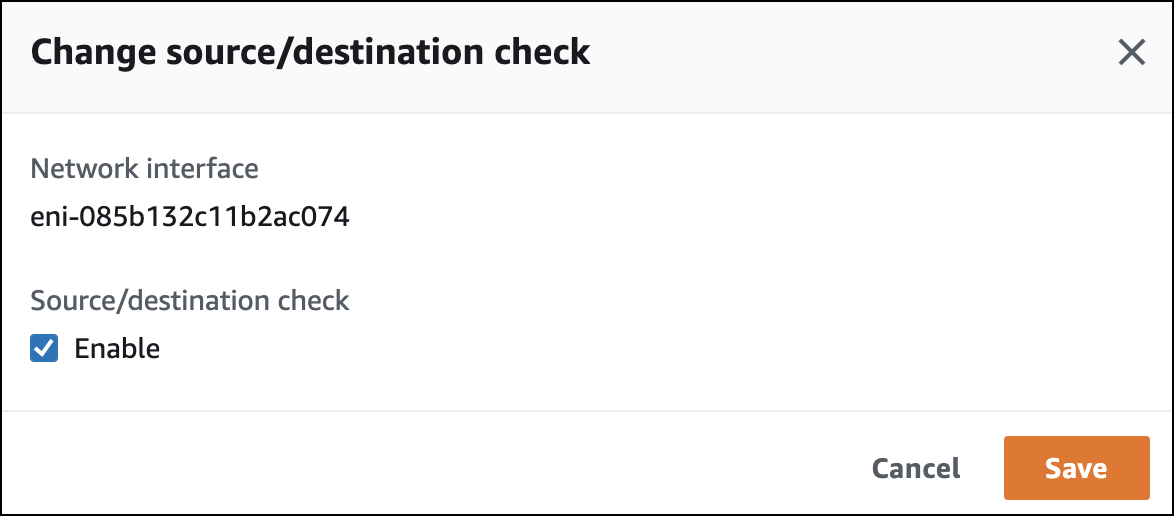
- Configure the Cisco CSR for the Umbrella tunnel.
a. Configure the WAN and the LAN interface.
interface GigabitEthernet1
ip address dhcp
negotiation auto
b. Create an IKEv2 proposal.
crypto ikev2 proposal umbrella
encryption AES-GCM-256
integrity SHA256 and SHA1
group 19 20
c. Create an IKEv2 policy.
crypto ikev2 policy umbrella
proposal umbrella
match address local <gigabitethernet-1-ip-address>
d. Create an IKEv2 keyring.
crypto ikev2 keyring umbrella
peer umbrella
address <umbrella-sig-tunnel-headend-ip-address>
pre-shared-key <umbrella-tunnel-password>
e. Create an IKEv2 profile.
crypto ikev2 profile umbrella
match identity remote address <umbrella-sig-tunnel-headend-ip-address>
identity local email <umbrella-tunnel-key-id>
authentication remote pre-share
authentication local pre-share
keyring local umbrella
dpd 10 2 periodic
f. Create an IPSec transform set.
crypto ipsec transform-set UMB_IPSEC_TRANSFORM_SET esp-gcm 256
mode tunnel
g. Link the IKEv2 profile and IPSec transform set.
crypto ipsec profile umbrella
set transform-set umbrella
set ikev2-profile umbrella
h. Create a tunnel interface.
interface Tunnel1
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel destination <umbrella-sig-tunnel-headend-ip-address>
tunnel protection ipsec profile umbrella
i. Create an interesting traffic access list.
ip access-list extended traffic_to_umbrella
permit ip any any
j. Create a route map.
route-map route_to_umbrella permit 10
match ip address traffic_to_umbrella
set interface Tunnel1
k. Apply the route map to LAN interface.
interface GigabitEthernet2
ip policy route-map route_to_umbrella
- Once the Cisco CSR configuration is complete and the tunnel is up, update the private subnet route table (SIG-VPC1-RT) to send all internet bound traffic to the LAN interface of the Cisco CSR.
Test the Cisco CSR Deployment
Once the Cisco CSR deployment is complete and the route table has been updated, the deployment is ready for testing. SSH to any instance in the VPC and run the curl http://ifconfig.co command. If everything is working as expected and you should get an IP address in the 146.112.x.x range back.
In addition, use the following commands on the Cisco CSR to verify the tunnel connectivity status and traffic processing:
show crypto isakmp sa
show crypto ipsec sa
show crypto engine connection active
debug crypto isakmp
debug crypto ipsec
Multiple AWS VPCs with Transit Gateway
In this setup, the customer has multiple VPCs running with a transit gateway providing interconnectivity between the VPCs. In this scenario, the transit gateway is typically coupled with a transit VPC to provide internet connectivity.
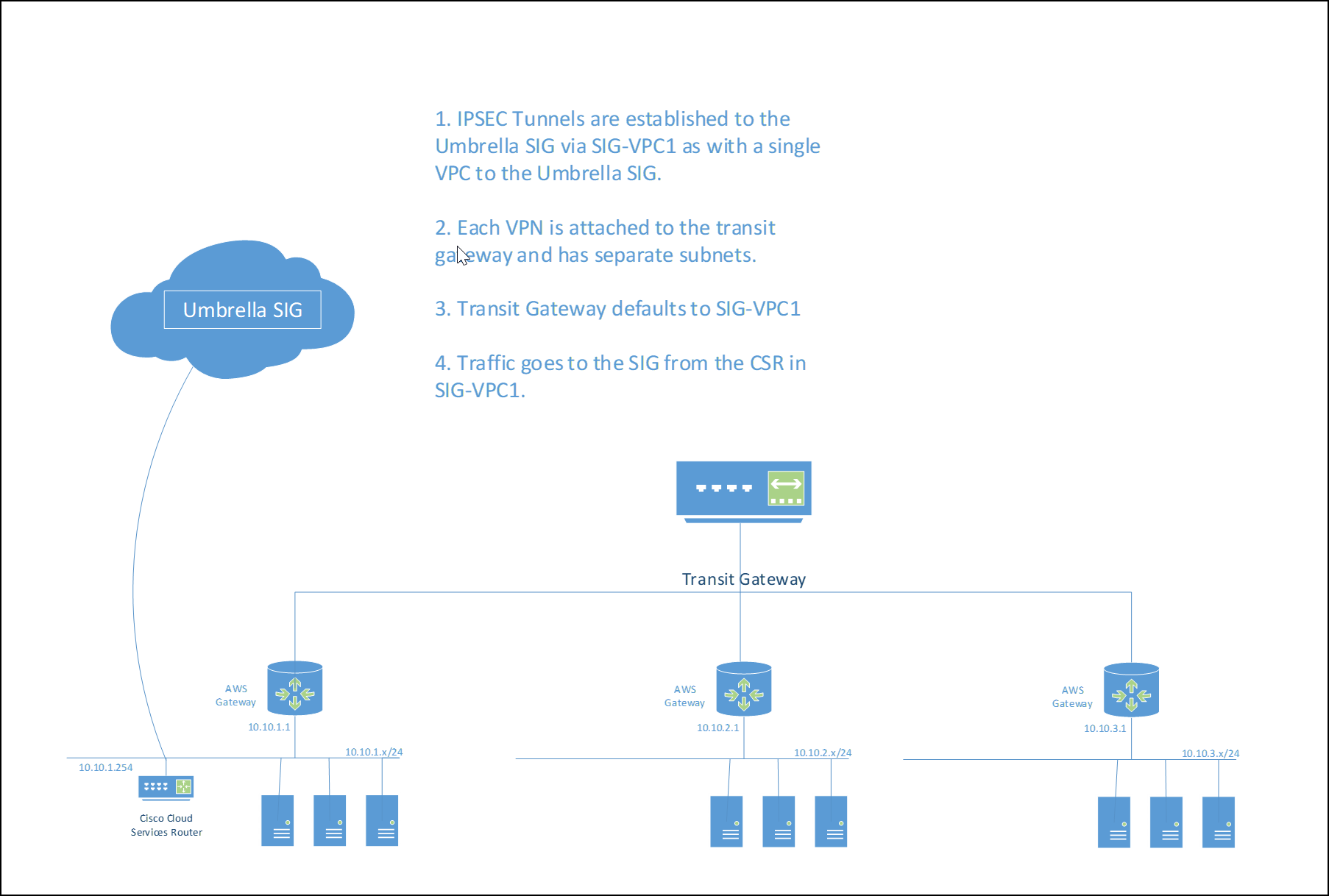
###Set Up the Transit Gateway
A Transit Gateway is an AWS entity to permit VPCs to communicate with other VPCs, network connections such a Peering Connections, VPNs, and so on. The transit gateway connects the customer VPNs to each other and defines a transit gateway route table.
Limitations
- Each VPC can have one or more subnets but the address space of each subnet must not overlap.
- Each VPC can have custom route tables; however, to traverse Umbrella through the CSR, the remote VPCs must route that traffic to the transit gateway through the AWS gateways.
Set Up the VPCs
First, deploy an SIG-VPC1. For more information and the procedure, see Set up the VPC with a Cloud Services Router (CSR). When deployed, create new server based VPCs.
- From the AWS dashboard, search for VPC and then Virtual Private Cloud Your VPCs Create VPC.
- Set the VPC Name Tag.
- In IPv4 CIDR block, set the subnet range.
Note: The VPCs must not be an overlapping IP address space or the conflicting VPC will not be able to be added.
VPC Name Tag IPv4 CIDR Tenancy SIG-VPC1 10.10.1.0/24 Default SERVER-VPC1 10.10.2.0/24 Default SERVER-VPC2 10.10.3.0/24 Default
Deploy and Configure the Transit Gateway
- From the AWS dashboard, search for VPC and then Transit Gateways > Create Transit Gateway. Label it
TRANSIT-GW. - Choose Transit Gateways > Transit Gateway Attachments > Create Transit Gateway Attachment and create the attachments. Each attachment will be a VPC attachment. Add SIG-VPC1, SERVER-VPC1 and SERVER-VPC2.
- Create two route tables in the newly deployed transit gateway, Transit Gateways > Transit Gateway Route Tables > Create Transit Gateway Route Table. Create a static route 0.0.0.0/0 and point it to the VPC for SIG-VPC1.
- In the VPC section Virtual Private Cloud Route Tables, edit the VPCs route tables.
For each of the SERVER-VPCs, their route table must be configured to point to the transit gateway as a default. This permits the SERVER-VPCs to communicate with all of the VPC subnets connected to the transit gateway.
As described in Step 6 of Set up the VPC with a Cloud Services Router (CSR), the static routes for the SIG IPSEC head ends will be in SIG-VPC1 already. Add static routes to each of the SERVER-VPCs to point to the transit gateway.
Test the Transit Gateway Deployment
Once the Cisco CSR deployment is complete and the route table has been updated, the deployment is ready for testing. Log in to any instance in the VPC using ssh and run the following command: curl <http://ifconfig.co>. If everything is working as expected, an IP address in the 146.112.x.x range is returned.
In addition, use the following commands on the Cisco CSR to verify the tunnel connectivity status and traffic processing:
show crypto isakmp sa
show crypto ipsec sa
show crypto engine connection active
debug crypto isakmp
debug crypto ipsec
Other Resources
Azure site to site VPN configuration guide
Umbrella Cloud Firewall
Cisco Cloud Services Router (CSR) 1000V
- Cisco CSR 1000v Deployment Guide for Microsoft Azure
- IOS IKEv2 Debugs for Site-to-Site VPN with PSKs Troubleshooting TechNote
Configure Tunnels with Palo Alto Prisma SDWAN < Configure Tunnels with Cisco Router in AWS > Configure Tunnels with Azure IPsec
Updated almost 2 years ago
