Connect Active Directory to Umbrella VAs
The Cisco Active Directory (AD) Connector monitors one or more domain controllers in your environment.
- The AD Connector listens to user and computer logins through the security event logs, and then transmits IP-to-user and IP-to-computer mappings to your deployed Umbrella Virtual Appliances (VAs).
- The AD Connector synchronizes user-to-group, computer-to-group and group-to-group memberships with Umbrella, which enables you to create and enforce group-based settings and view user, computer, and group-based reports.
The AD Connector helps import your Active Directory (AD) users, groups and computers to provide these mappings. Other AD objects, including Organization Units (OUs), are not imported.
Note: Only one AD Connector is required for each Umbrella site. For redundancy, add an optional second connector. If you are adding multiple AD domains through domain controller integrations, one connector is required per AD domain per Umbrella site, with an optional second connector for redundancy if required.
This guide describes the steps to install the Cisco AD Connector for LDAP or LDAPS, and provision users and groups from your instance of Microsoft AD to Umbrella.
How to Configure the Setup of the AD Connector
The deployment of the AD Connector has various components. You can configure the Cisco AD Connector to provision users and groups from Microsoft AD using LDAP or LDAPS (domain controller or domain).
- (Optional) Configure authentication for the AD Connectors in your environment. For more information, see Configure Authentication for AD Connectors and VAs.
- Download the AD Connector ZIP file from Umbrella.
- Add a domain controller or domain in Umbrella for LDAP or LDAPS deployments.
- Install and configure the AD Connector on your server.
- Verify that the AD Connector begins to provision users and groups in Umbrella.
Table of Contents
- Prerequisites
- (Optional) Specify AD Groups of Interest
- Install the Connector
- Verify That the Connector Syncs with Umbrella
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- For information about the requirements for deploying the AD Connector, see Prerequisites for AD Integration with VAs.
- (Optional) Configure Authentication for the AD Connectors and VAs.
- Prepare Your Active Directory Environment.
(Optional) Specify AD Groups of Interest
You can optionally specify AD groups of interest for the purpose of policy creation in Umbrella. This is to avoid synchronizing all your AD groups to Umbrella and is recommended for easier policy management.
Rename Selective Sync File After Upgrading to AD Connector v1.14.4
If you use selective sync and upgrade the Cisco AD Connectors to v1.14.4 or later, you must rename the current selective sync file C:\CiscoUmbrellaADGroups.dat to C:\CiscoADGroups.dat.
Note: The selective sync file—previously named CiscoUmbrellaADGroups.dat—is not recognized by the Cisco AD Connector v1.1.4.4 or later.
After you rename the selective sync file, Umbrella automatically reads the selective sync file (C:\CiscoADGroups.dat) and syncs the Users in the specific Groups from AD to Umbrella. You are not required to restart the AD Connector service.
Create AD Groups in a Selective Sync File
- Identify the AD groups of interest. Users and computers belonging to these groups will be synchronized to Umbrella.
For each sub-tree, only the parent group needs to be specified. All AD groups, users, and computers that are part of this parent group will automatically be included.
Note: If Selective Sync is enabled, AD Users and Computers that are not members of Groups specified in CiscoADGroups.dat or their sub-groups will not be synchronized to Umbrella and will be completely exempt from Umbrella Policies and Reporting. - Create a CiscoADGroups.dat file in the C:\ drive of each machine where the connector will be installed.
The connector only reads the C:\CiscoADGroups.dat file. If the file is incorrectly named or is not present in the C:\ drive, all groups will be imported to Umbrella. - List the AD groups that need to be synchronized in distinguished name (DN) format in this file.
Get-ADGroup -Identity <ADGroupName>
Supported OUs
Not Supported: OU=My OU,OU=Organizational Unit,DC=sample,DC=local
Supported: CN=My Group,OU=Organizational Unit,DC=sample,DC=localSample file entries:
- CN=Engineering,CN=Builtin,DC=ciscoumbrella,DC=com
- CN=Sales,CN=Builtin,DC=ciscoumbrella,DC=com
- CN=Marketing,CN=Builtin,DC=ciscoumbrella,DC=com
- Ensure that there are no blank lines anywhere in the file.
Note: If you are running multiple connectors, the C:\CiscoADGroups.dat file should be present on each system running the connector and should be identical on each system.
Total Number of Groups Selected for Synchronization
The total number of groups selected for synchronization—groups specified in the selective sync file and all their sub-groups—should not exceed 15,000. Also, these groups should not be nested within more than five OU levels. Selective synchronization fails in both cases. If either of these requirements cannot be met, the selective sync file should not be used so that a full AD tree synchronization can be done instead.
Install the Connector
The connector can be installed on a domain controller or a server that is a member of the domain. For more information, see Prerequisites for AD Integration with VAs. Also, verify that network connectivity requirements specified in Communication Flow and Troubleshooting are met.
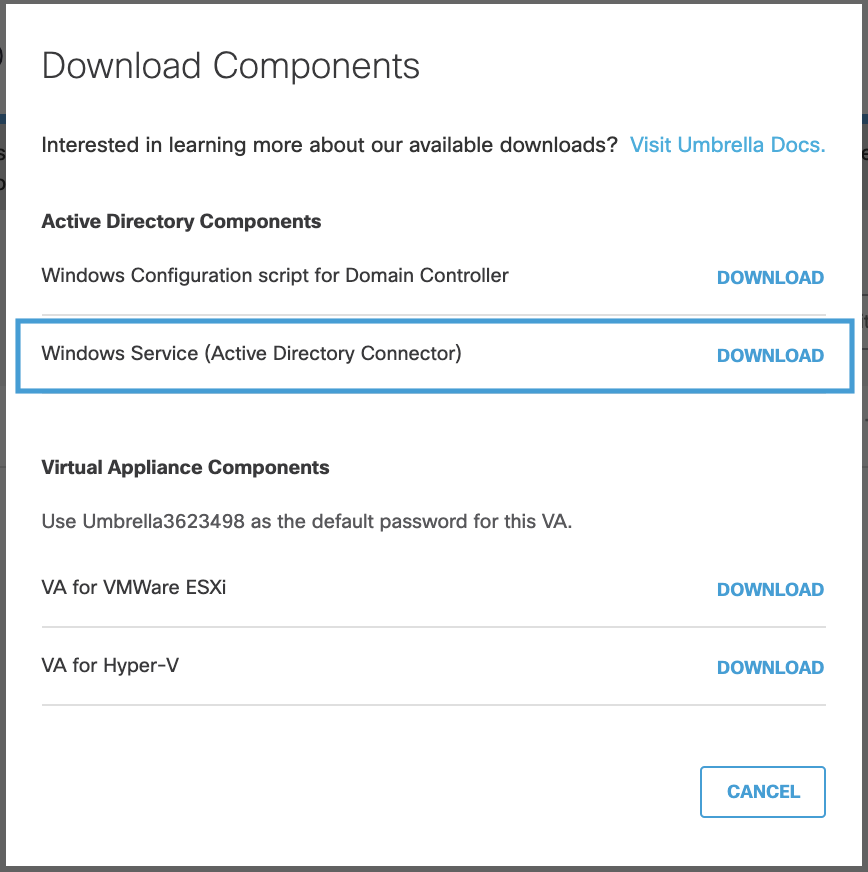
- In the Umbrella dashboard, navigate to Deployments > Configuration > Sites and Active Directory and click Download.
- Click DOWNLOAD for Windows Service (Active Directory Connector).
Note: You must download the ZIP file to the local machine where you plan to run it or copy it locally from another machine. We do not recommend that you install the connector from a network drive or run the Setup.msi directly from the compressed file.
-
As an administrator, extract the contents of the Cisco-Windows-Service ZIP file that you downloaded from Secure Access to a folder on the server, and then navigate to that folder.
Note: If you run the AD Connector installer files from the root directory of your server, you may encounter installation errors. -
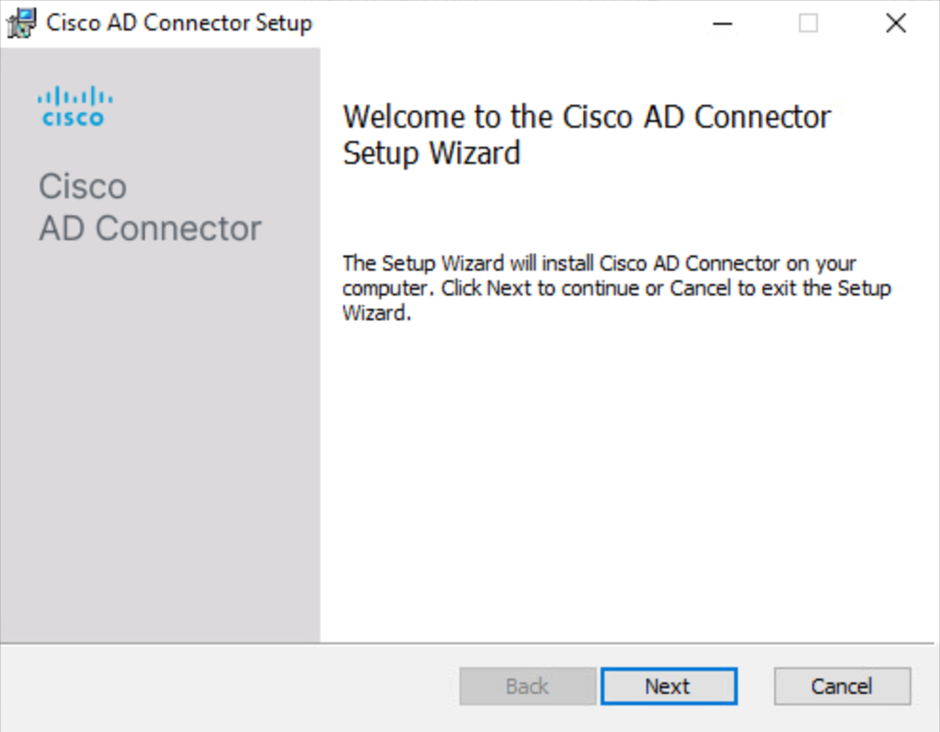
Run Setup.msi, and then in the Cisco AD Connector Setup wizard, click Next.
-
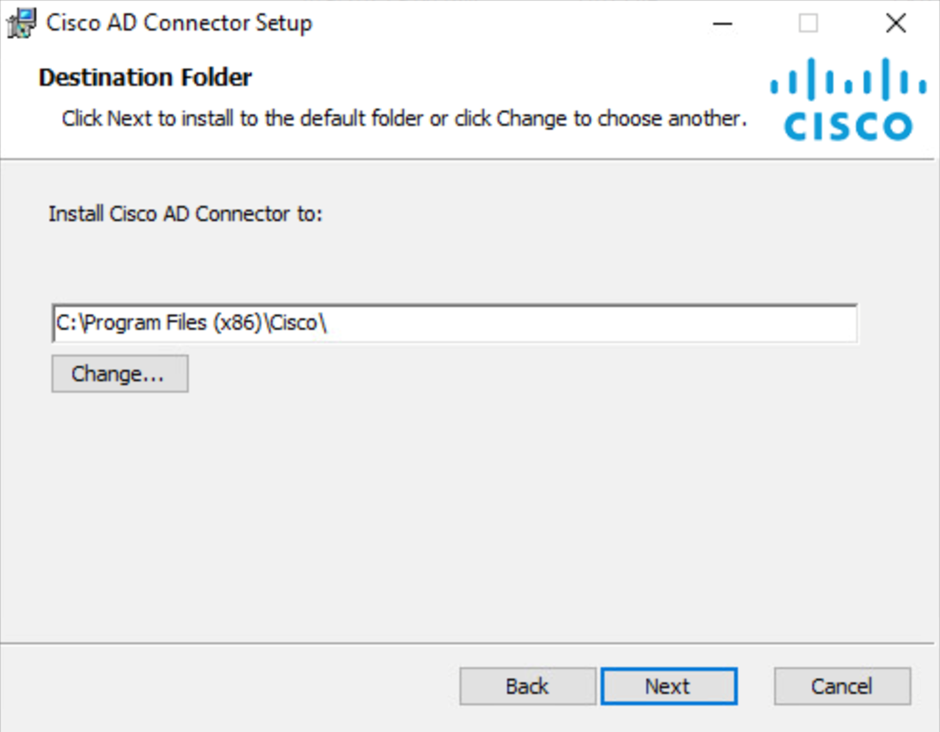
Choose the directory on the server to install the Cisco AD Connector and then click Next.
-
Select AD Lookup (using LDAP/LDAPS) and then click Next to provision identities using LDAP lookup of the Domain Controller or Domain registered on the same site.
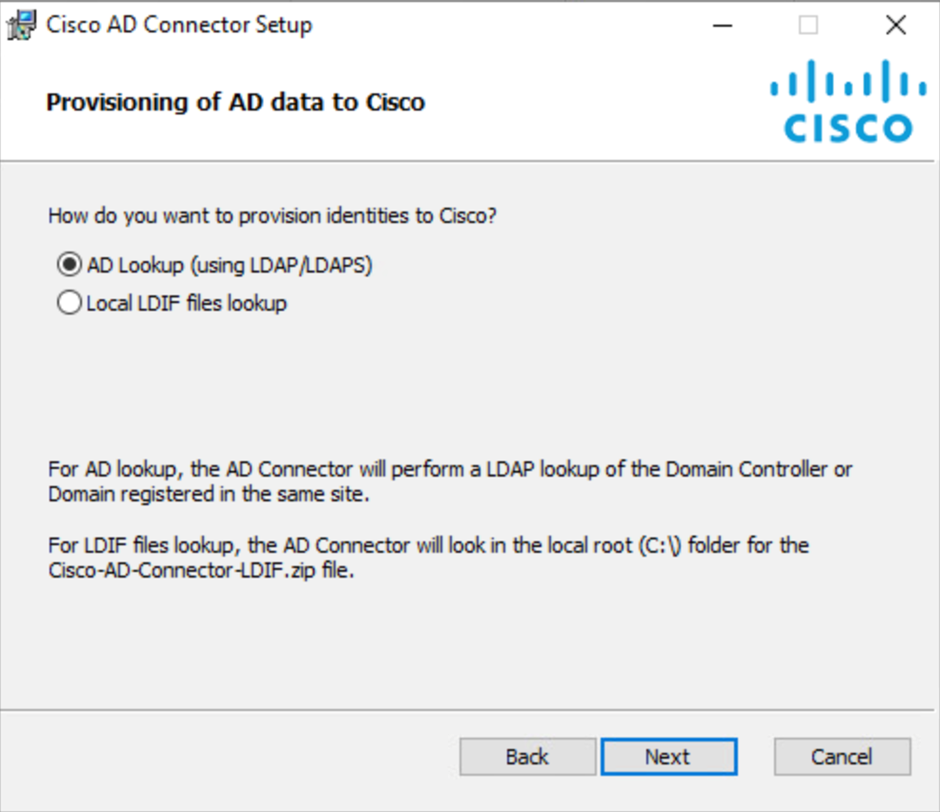
You can also select Local LDIF files lookup to provision identities using Cisco-AD-Connector-LDIF.zip file in the local root folder. To use this option refer to Deploy LDIF Files for AD Connector.
-
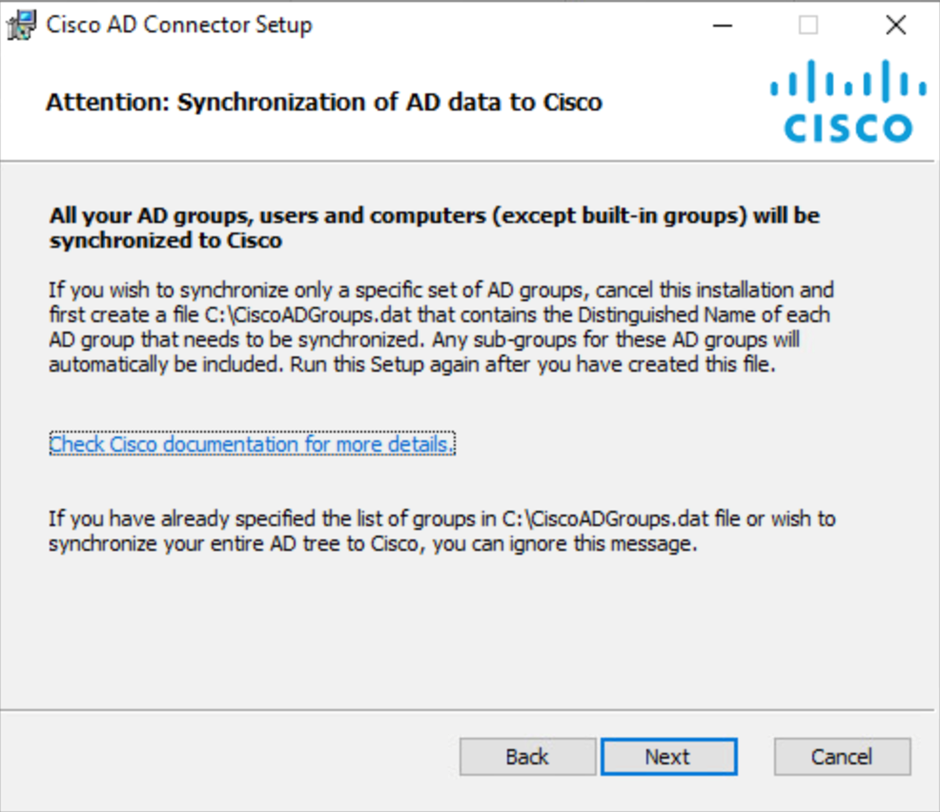
Click Next to confirm that you permit your AD Users and Groups to sync to Secure Access from the Cisco AD Connector.
-
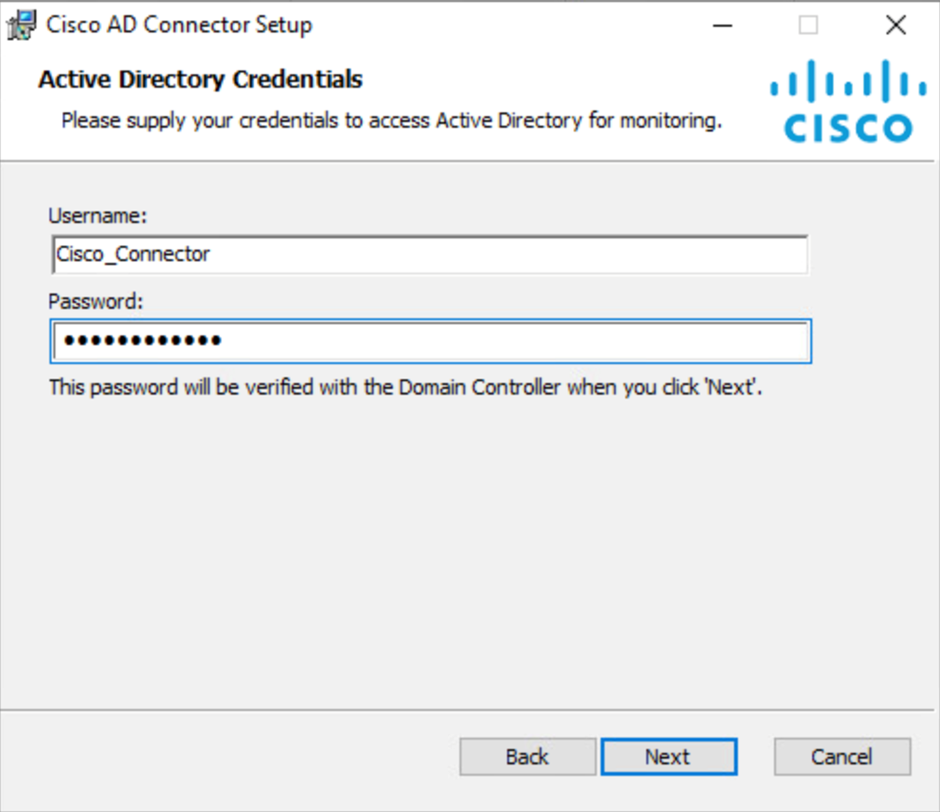
Add your Active Directory credentials. Enter the Username of the Cisco AD Connector user (Cisco_Connector or custom username), the Password, and then click Next. For more information, see Prerequisites.
-
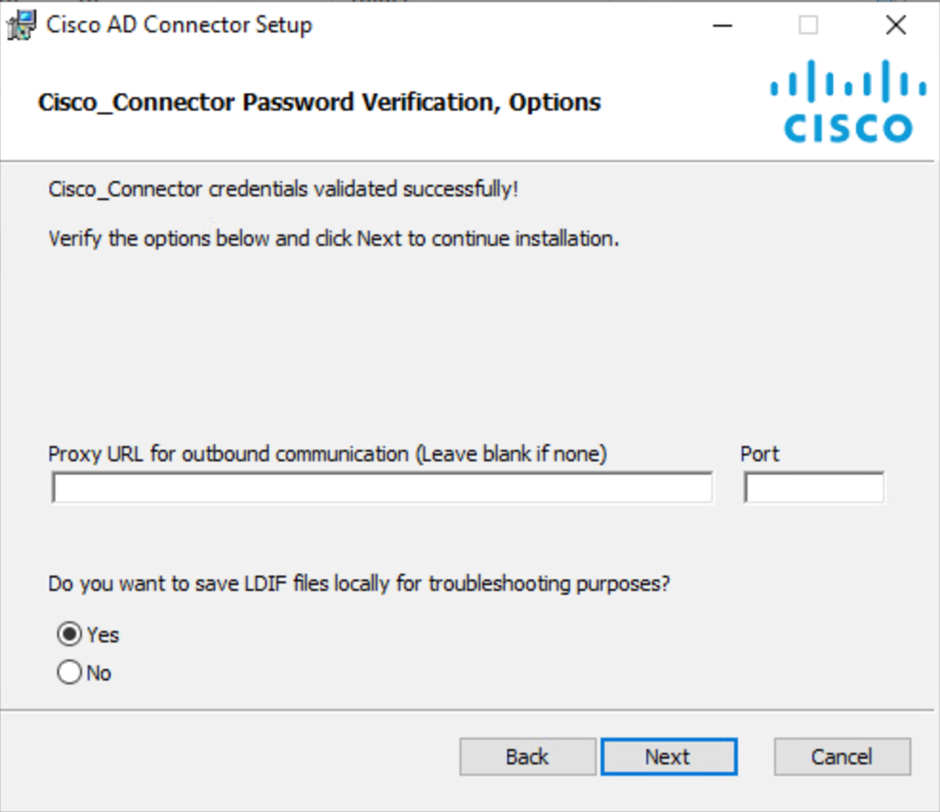
(Optional) Enter the Proxy URL and port for the outbound communication.
-
(Optional) Choose the appropriate option if you want to save LDIF files locally.
-
Click Next and then click Install.
-
Once the setup is complete, click Finish.
Return to the Umbrella dashboard. Verify that the Cisco AD Connector is in the same Umbrella site as the domain controller or domain that it needs to communicate with.
Verify That the Connector Syncs with Umbrella
- For more information, see View AD Components in Umbrella.
Prepare Your Active Directory Environment < Connect Active Directory to Umbrella VAs > Multiple Active Directory and Umbrella Sites
Updated 5 months ago
