Cisco Secure Client (Android OS)
DNS Policies Only
Android Mobile Security is only supported in Umbrella for DNS policies.
Mobile device threats are prevalent on any network. The Cisco Secure Client with Umbrella module is a roaming client for managed Android devices that offers protection from these threats at the DNS layer. This protection extends to both apps and browser-based traffic to the entire protected scope of the Android device.
A mobile device management system (MDM) is required to deploy the Cisco Secure Client to mobile devices and to push the Umbrella configuration to the mobile devices.
Device Security
There are two deployment modes for the Cisco Secure Client with Umbrella module:
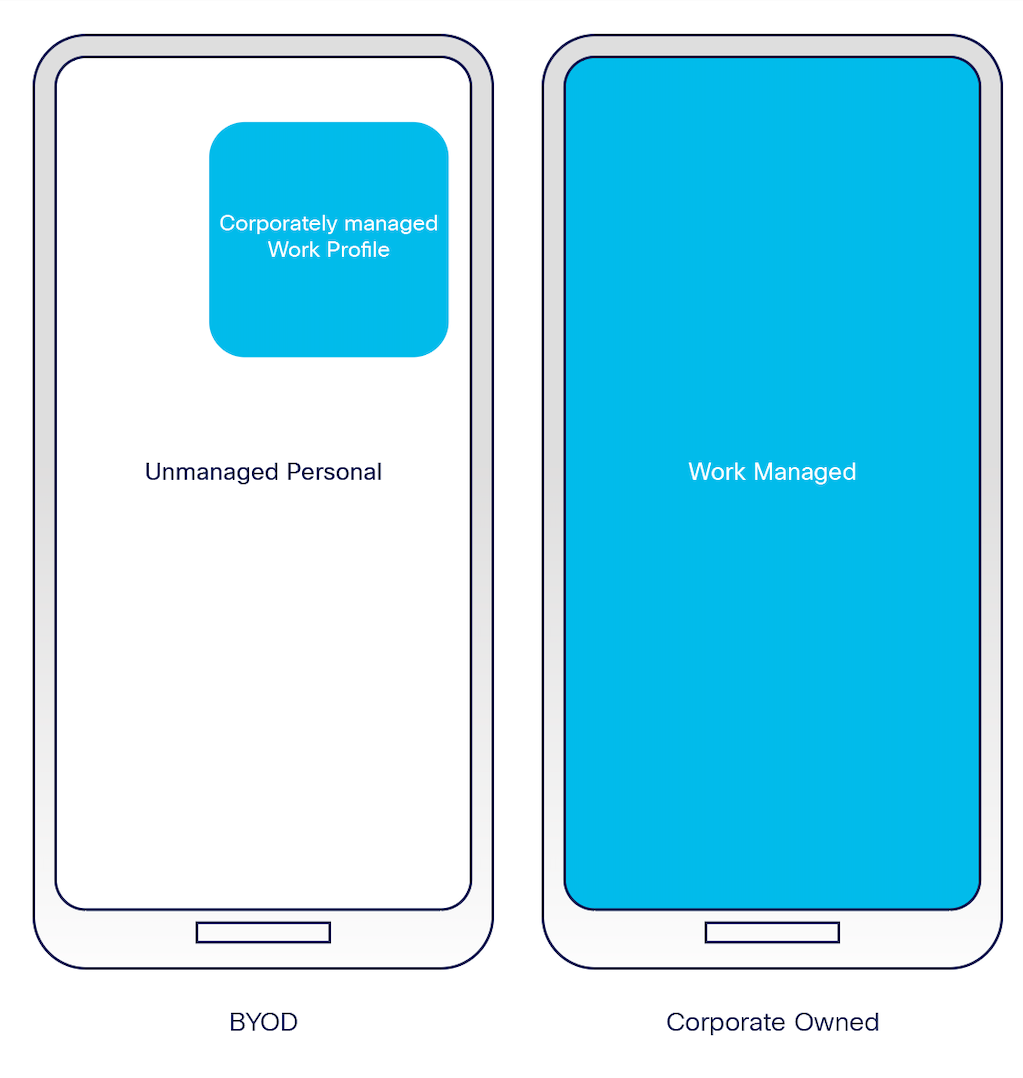
- Personal "bring your own device" (BYOD)
- Organization-owned device
Umbrella coverage applies exclusively to the work profile of the Android device. For fully managed (organizational owned) devices, the entire device is covered. For employee-owned devices with a work profile, only the work profile is covered by Umbrella for Android. Please refer to the diagram below, where blue indicates Umbrella coverage:
Prerequisites
- An Android Enterprise compatible device deployment. The legacy Device Admin (DA) system is not supported at this time
- Private DNS must be turned off for DNS interception to function properly.
- Android mobile devices running Android OS version 6.0.1 and above. Devices examples are Samsung, Google, and Motorola. FireOS devices and other Android forks are not supported.
- An MDM for deploying the software. The following MDMs have been tested, and you should be able to use any MDM:
- MobileIron
- Meraki
- VMWare WorkspaceOne (Airwatch)
- Microsoft InTune
- Samsung Knox
- Google Admin Console (Google Workspace)
- Access to an Umbrella subscription including mobile device coverage
- A network meeting access requirements
- For IPv4 or Dual Stack networks, ensure that UDP ports 53, 5353, and 443 are accessible to the IP address 208.67.222.64.
- For IPv6 or Dual Stack networks, ensure that UDP ports 53, 5353, and 443 are accessible to the IP address 2620:119:53::64.
Note: For IPv6-only networks, the NAT64 and DNS64 or 464XLAT gateways are required.
*DNS64 (RFC 6147) is meant for single-stack IPv6 networks. This is to help with IPv4 to IPv6 transitions. If you are using Umbrella DNS on devices without IPv4 access, these resolvers will synthesize records that can reach those destinations through a NAT64 gateway using the Well-Known Prefix. More details available in DNS64: DNS Extensions for Network Address Translation from IPv6 Clients to IPv4 Servers.
- For on-network scenarios, Trusted Network Detection (TND) may also be used to disable the client on network and pass traffic to a Virtual Appliance. The following prerequisites apply:
- All VAs in use are defined by FQDN (IPs do not allow the client to go into trusted network mode) in the
umbrella_va_fqdnsconfiguration property.- The format for this field is comma separated, for example, (va1.domain.com, va2.domain.com)
- VAs must be registered to the same Umbrella organization as the Android devices
- HTTPS mode for user events enabled on the Virtual Appliance
- If the VA’s FQDN is not publicly signed, the self-signed root certificate for the VA domain used for HTTPS mode on the VA must also be pushed to the Android device to sign the connection.
- VA certificates should contain Subject Alternate Name (SAN) matching the VA’s configured domain to successfully communicate with the VA over HTTPS mode
- For more information on how to configure HTTPS mode on the VA, see Umbrella Virtual Appliance: Receiving User-IP mappings Over a Secure Channel.
- All VAs in use are defined by FQDN (IPs do not allow the client to go into trusted network mode) in the
Known Issues
The app download may fail in the Google Play store after enabling the Cisco Secure Client with Umbrella module. This is a known limitation from Google on Android OS. To avoid this, download the apps before enabling the Umbrella module. Google has fixed this behavior in Android OS “Q”. For more information, see the Google issue tracker.
Some features may not work correctly on Huawei devices. For more information, see Troubleshooting and the Frequently Asked Questions.
Cisco Secure Client (Android OS) > Deploy the Android Client
Updated about 1 year ago
