Configure AD FS for SAML
Active Directory Federated Services (AD FS) for SAML configuration can be authenticated one of two ways: by uploading the identity provider's (IdP) metadata file, or by manually configuring with specific IdP fields.
Table of Contents
- Prerequisites
- Configure AD FS
- Configure AD FS for SAML in Umbrella with Metadata Upload
- Configure AD FS for SAML in Umbrella Manually
Prerequisites
- id.swg.umbrella.com must be sent to the Umbrella secure web gateway (SWG) and not sent directly to the internet.
- SAML metadata must have a signing key.
- Ensure that your IDP Endpoint (the URL used to communicate with your identity provider) bypasses the Umbrella proxy to avoid an authentication loop.
- Configure SAML with your identity provider (IdP) that supports SAML 2.0 POST profiles.
- Download your IdP's metadata file in XML format.
- Enable cookies for your browser.
- Enable SAML and HTTPS inspection on a Ruleset that includes the Network and Tunnel identities from which the user traffic arrives.
Configure ADFS
- Log into AD FS and navigate to Server Manager > Tools > AD FS Management.
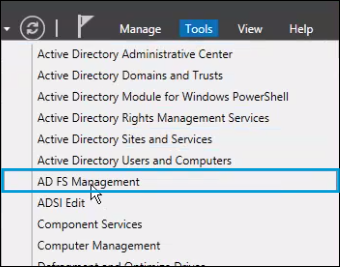
- In the AD FS Manager, right-click on Trust Relationships and navigate to Relying Party Trusts > Add Relying Party Trust and select Start.
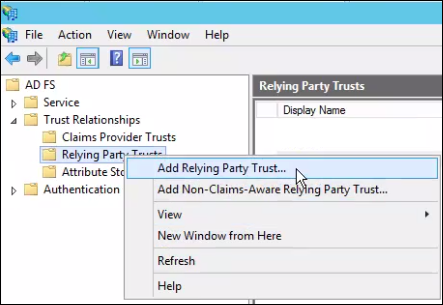
- Choose Import data about the relying party from a file and browse for the metadata.xml file downloaded from Umbrella.
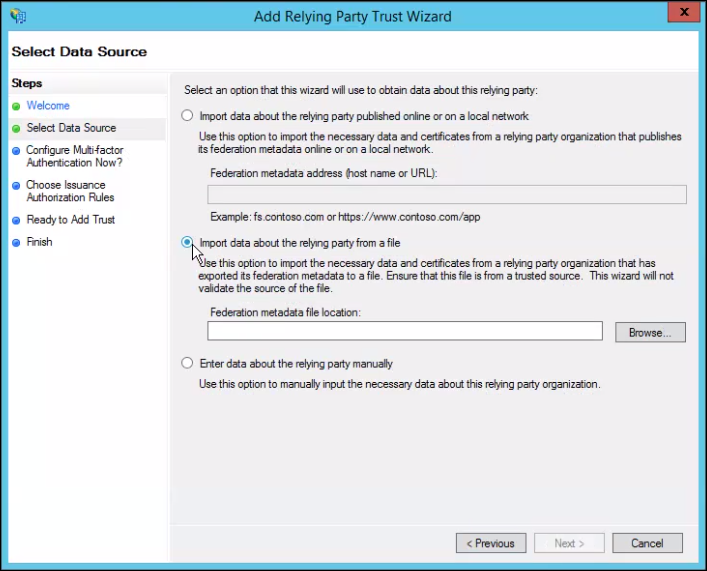
- Provide a meaningful name for the trust connection and click Next.
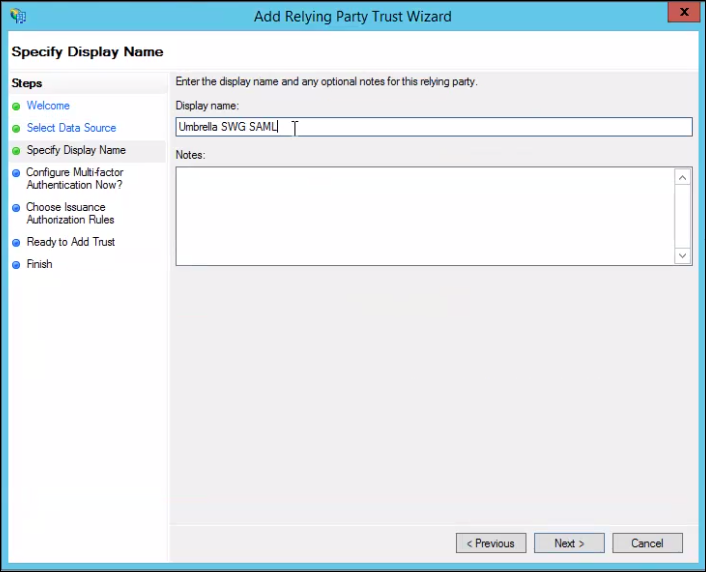
- Select I do not want to configure multi-factor authentication settings for this relying party trust at this time and click Next.
- Select Permit all users to access relying party and click Next.
- Verify settings and click Next.
- Right-click on the recently created relaying party and select Edit Claim Rules.
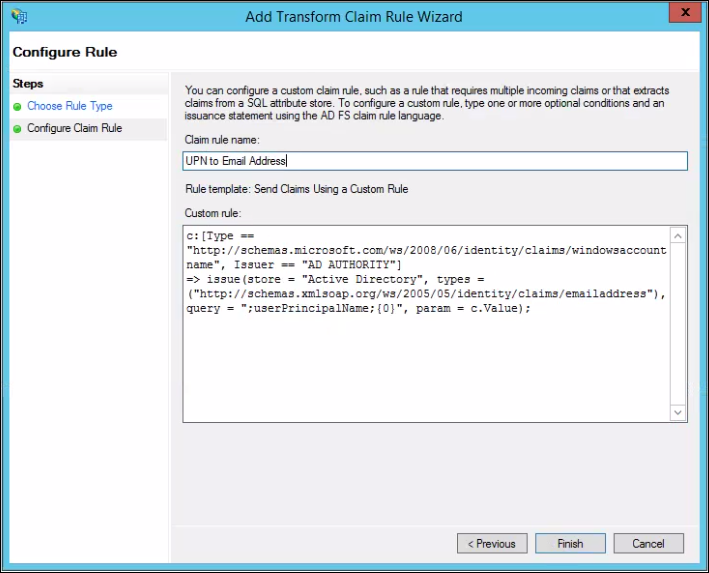
- Under Issuance Transform Rules, click Add Rule, then choose Send Claims Using a Custom Rule with the following configuration:
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"), query = ";userPrincipalName;{0}", param = c.Value);
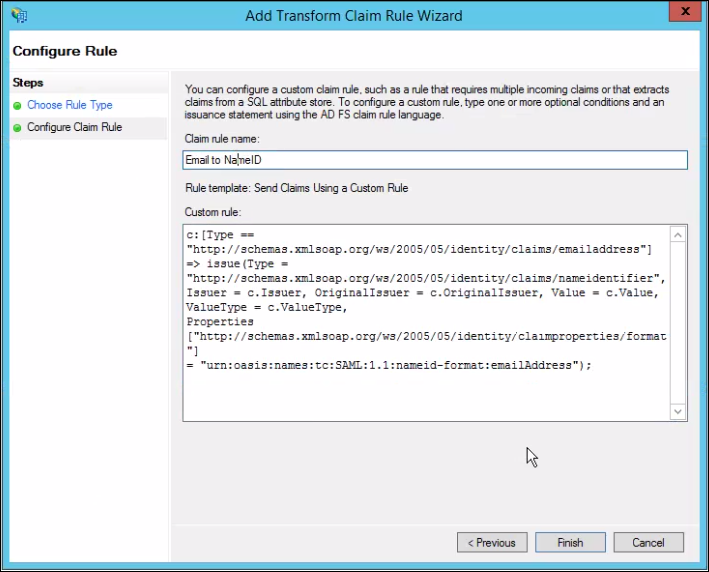
- Repeat step 7 with the following configuration.
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress");
Configure AD FS for SAML in Umbrella with Metadata Upload
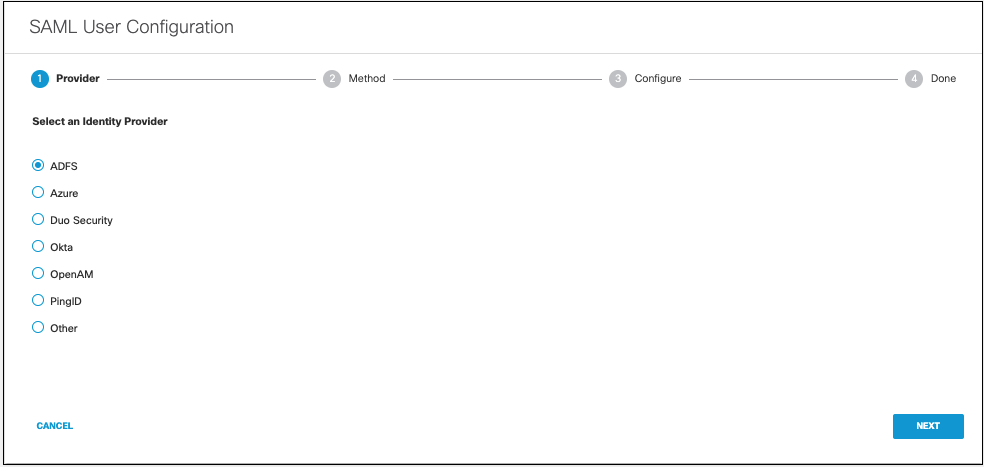
- Navigate to Deployments > Configuration > SAML Configuration and click Add.

- Select ADFS and click Next.
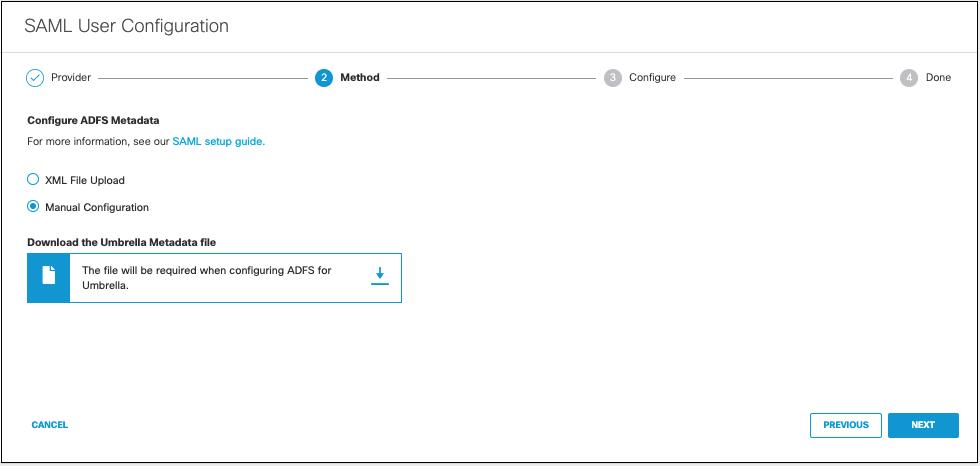
- Select XML File Upload.
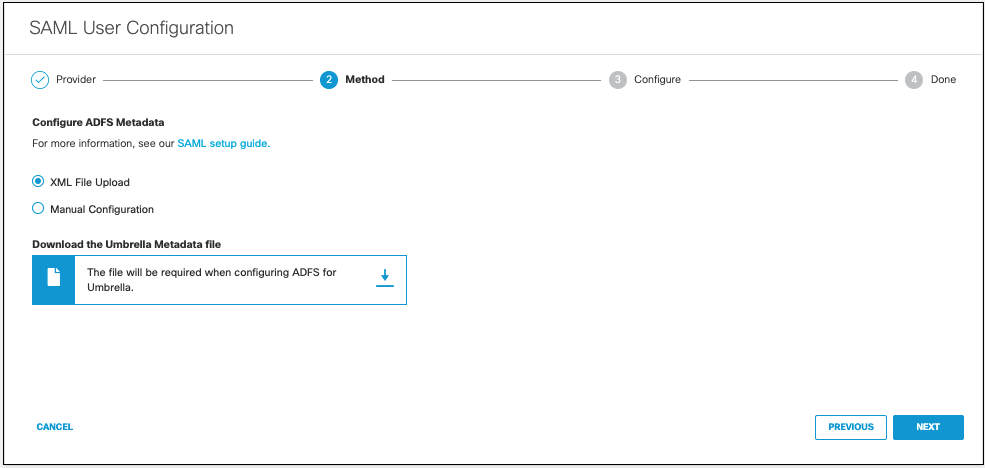
- Download the Umbrella metadata file (SP metadata file) and click Next.
The Umbrella SP metadata includes the Service Provider Issuer ID, the assertion consumer endpoint URL information, and the SAML request signing certificate from Cisco Umbrella. This metadata is required when configuring your IdP for Umbrella.
Note: Your IdP must send the Cisco Umbrella User Principal Name in the NameID attribute in the SAML assertion. For more information on configuring your IdP, exporting your IdP metadata, obtaining your IdP details, or downloading your IdP signing certificate, refer to your vendor's documentation.
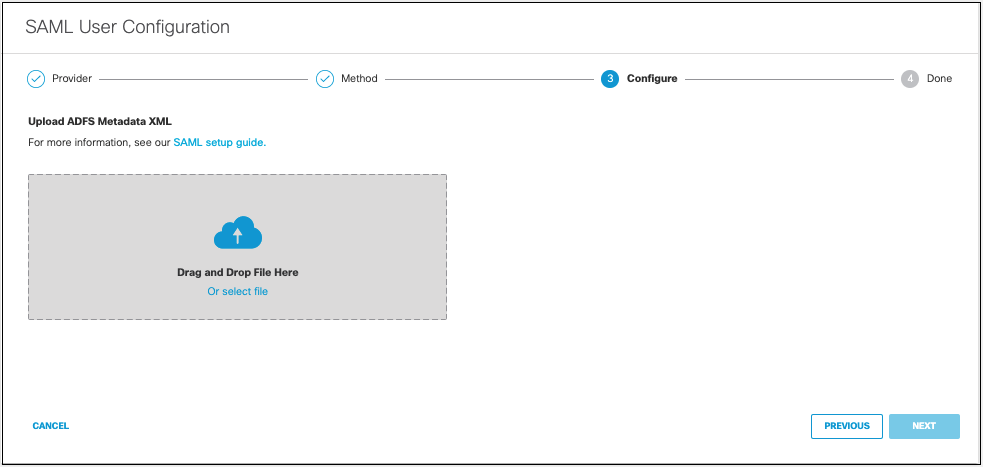
- Upload your IdP's metadata file in XML format and click Next.
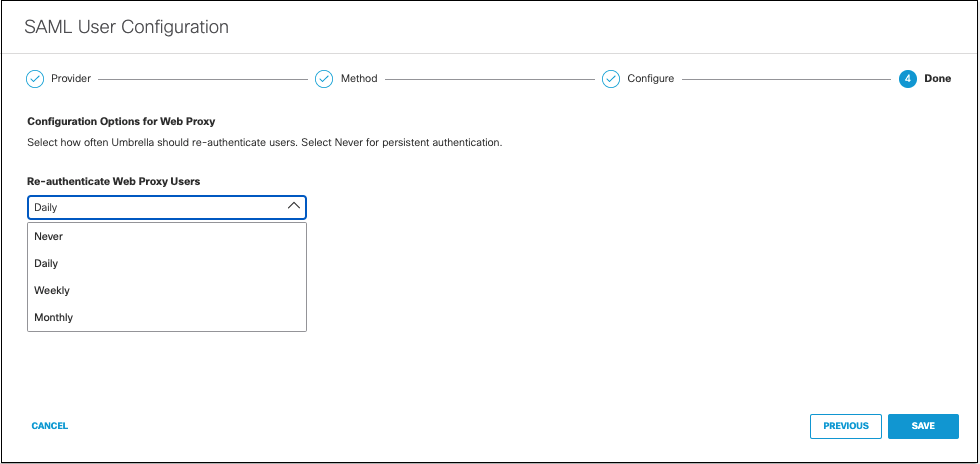
- From the Re-Authenticate Users drop-down list, choose how often Umbrella re-authenticates users: Never, Daily, Weekly, or Monthly.
- Click Save. Your new configuration appears as SAML Web Proxy Configuration.
Configure AD FS for SAML in Umbrella Manually
- Navigate to Deployments > Configuration > SAML Configuration and click Add.

- Select ADFS and click Next.
- Select Manual Configuration.
- Download the Umbrella metadata file (SP metadata file) and click Next.
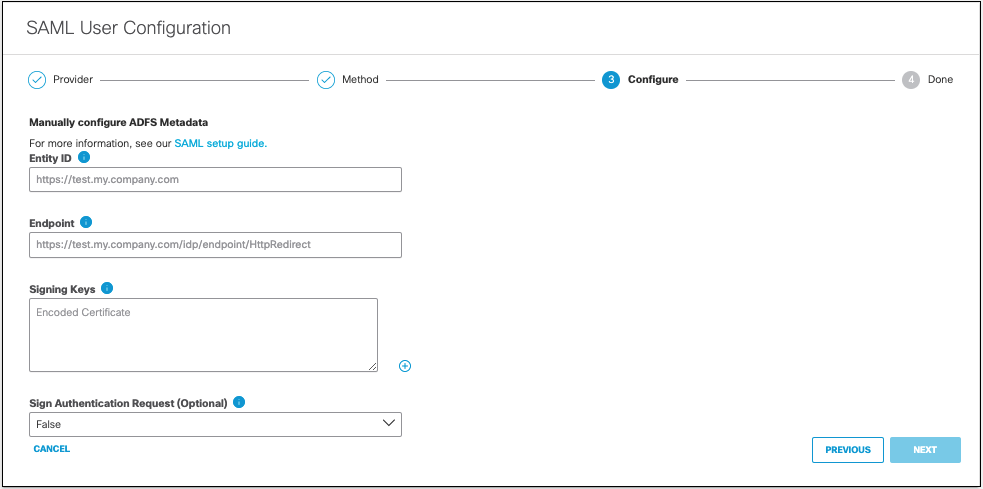
The Umbrella SP metadata includes the Service Provider Issuer ID, the assertion consumer endpoint URL information, and the SAML request signing certificate from Cisco Umbrella. This metadata is required when configuring your IdP for Umbrella. - Enter the appropriate information to configure ADFS's provider metadata and click Next.
- Entity ID—A globally unique name for an identity provider.
- Endpoint—The URL used to communicate with your identity provider.
- Signing Keys—Your identity provider’s x.509 certificate used to sign the authentication request.
- Signed Authentication Request (optional)—You can sign the authentication request for this IdP.
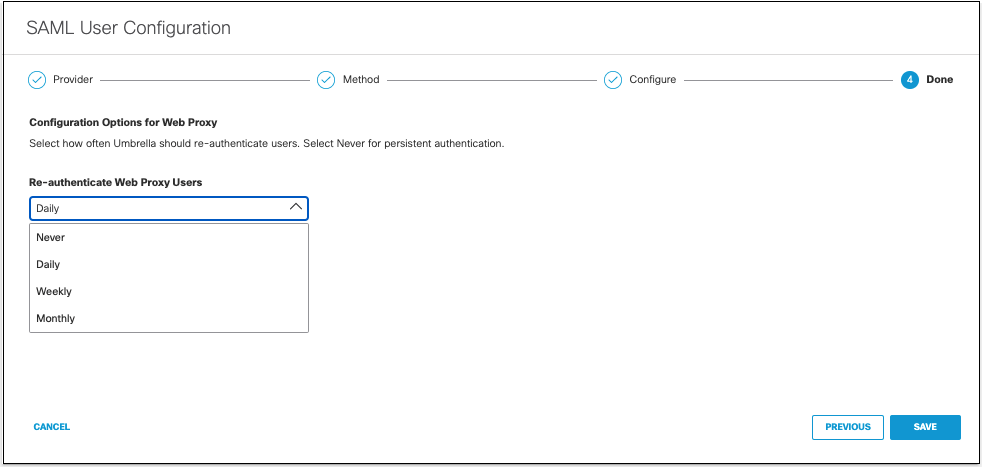
- From the Re-Authenticate Users drop-down list, choose how often Umbrella re-authenticates users: Never, Daily, Weekly, or Monthly.
- Click Save. Your new configuration appears as SAML Web Proxy Configuration.
Configure Okta for SAML < Configure AD FS for SAML > Configure Duo Security for Cisco Umbrella SAML
Updated over 1 year ago
