(Unpublished) Configure Tunnels with AWS Native IPsec
INTERNAL DOCS TEAM NOTE
Unpublished this November 2022 because the SIGINT team discovered problems with this method. PM has decided it's not supported at this point. We can turn it back on if/when whatever work needs to be done gets completed.
Use the AWS native VPN gateway to establish tunnels to Umbrella. This configuration assumes that a VPC is already deployed.
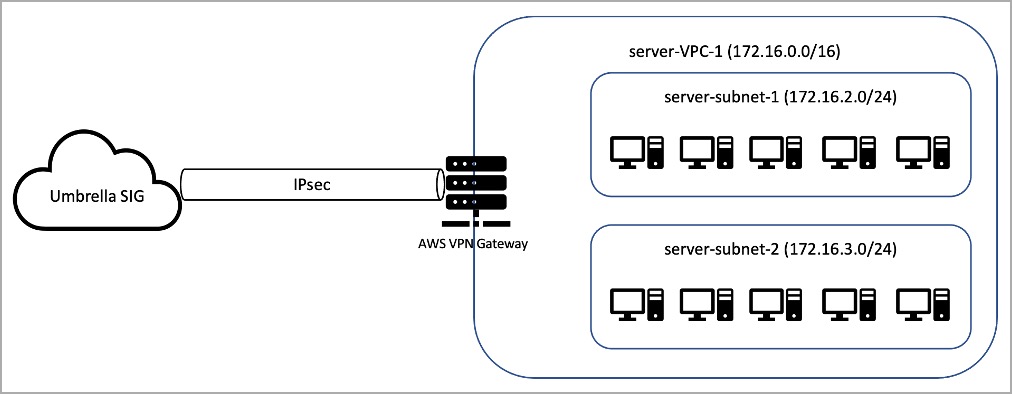
Table of Contents
- Create the AWS Virtual Private Gateways
- Create Customer Gateways
- Create AWS Site-to-Site VPN Connection
- Update Route Tables
- Configure Umbrella Private Access Tunnel
- Appendices
Create the AWS Virtual Private Gateways
- Navigate to VPC > Virtual private network (VPN) > Virtual private gateways > Create virtual private gateway.
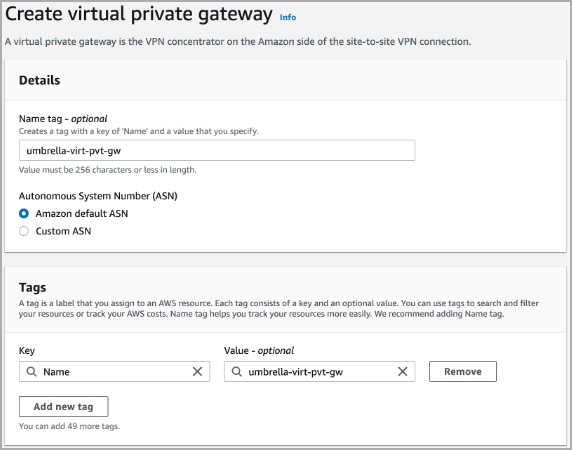
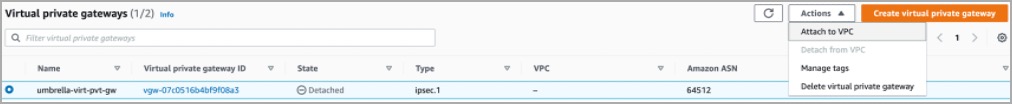
- Once configured, attach the Virtual private gateway to your VPC. Click the Actions drop-down and select Attach to VPC.
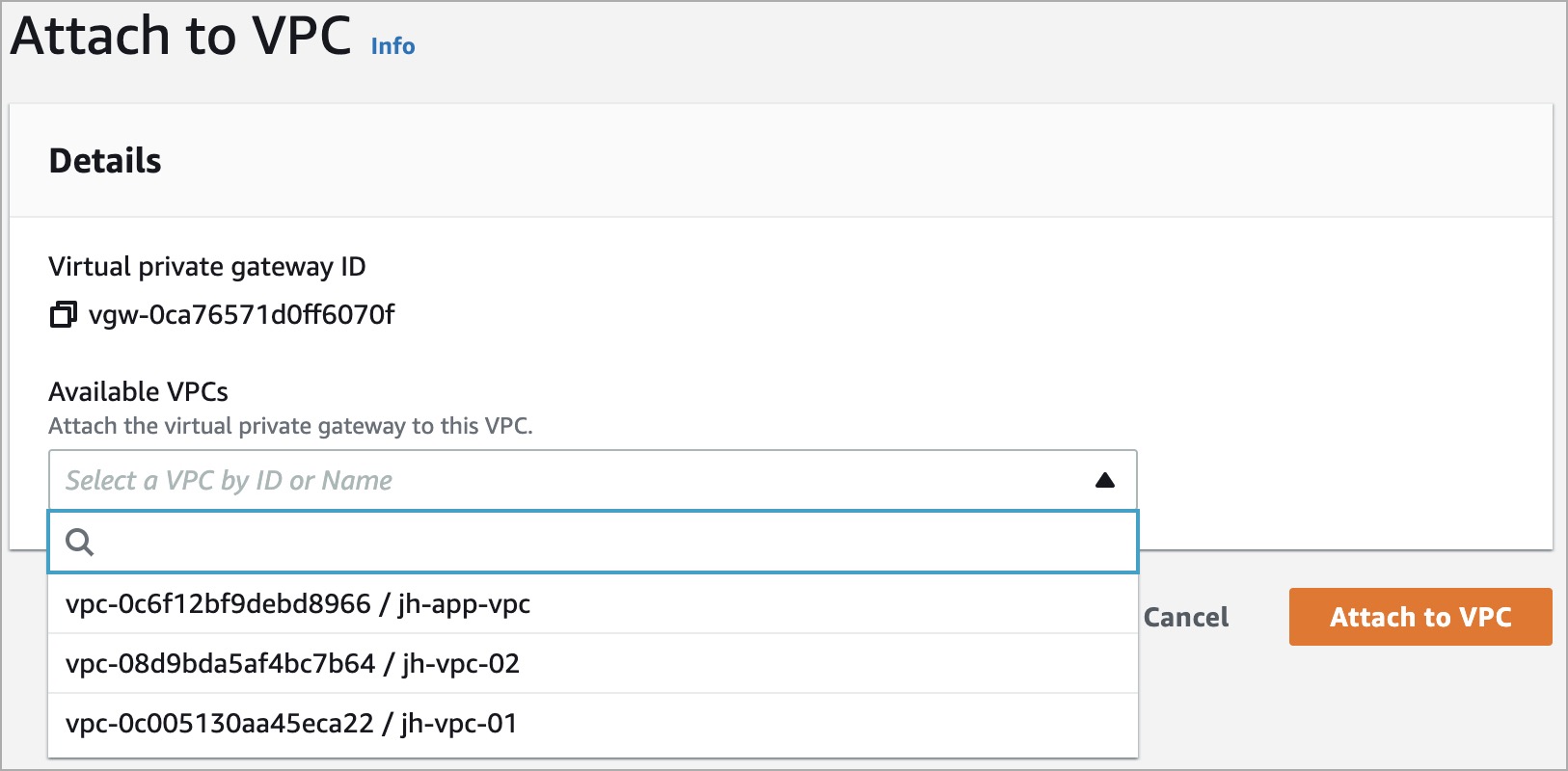
- Select the VPC from the drop-down list.
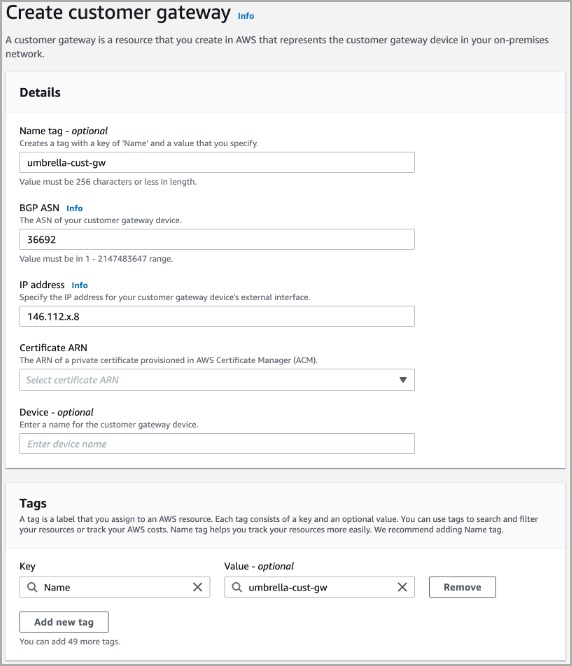
Create Customer Gateways
- Navigate to VPC > Virtual private network (VPN) > Customer gateway > Create customer gateway.
- Configure BGP ASN to be the Umbrella ASN 36692.
- Identify the nearest Umbrella DC IP address and enter the same in the IP address field.
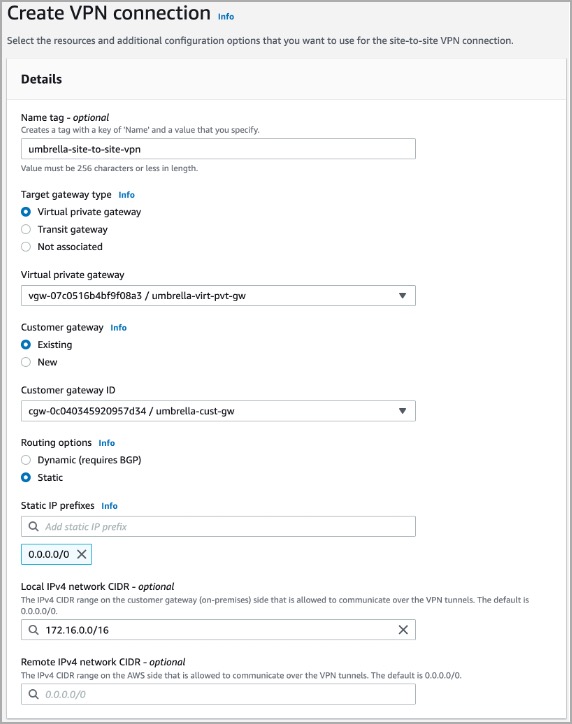
Create AWS Site-to-Site VPN Connection
- Navigate to VPC > Virtual private network (VPN) > Site-to-Site VPN Connections > Create VPN connection.
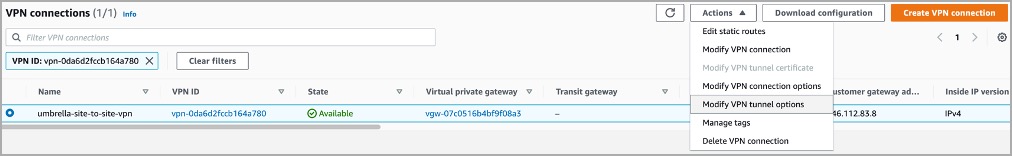
- Once the VPN tunnel is configured, click Modify VPN tunnel options.
- Select the egress IP address of the site-to-site VPN.
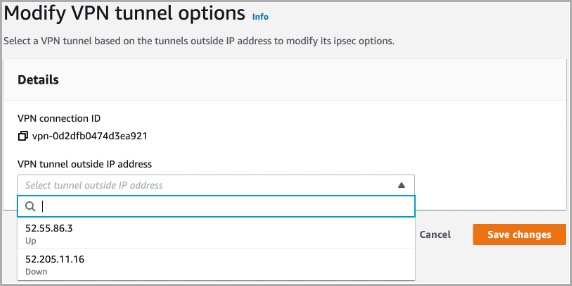
4. Copy the Pre-shared key and save it on your device.
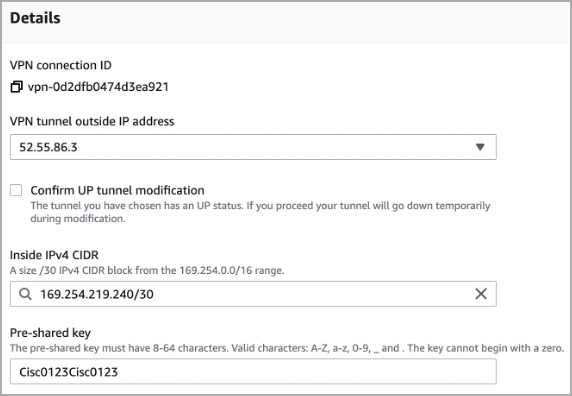
- Configure the VPN parameters as shown below:
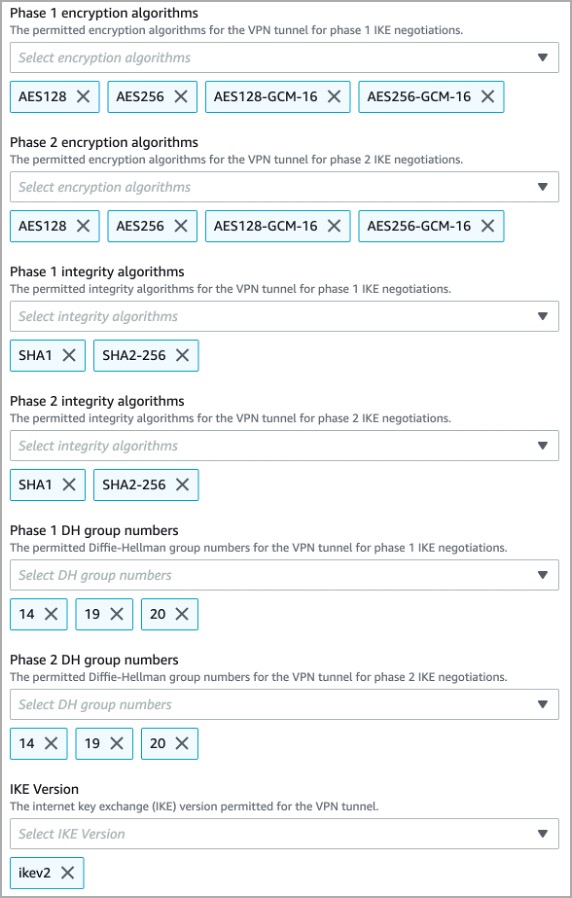
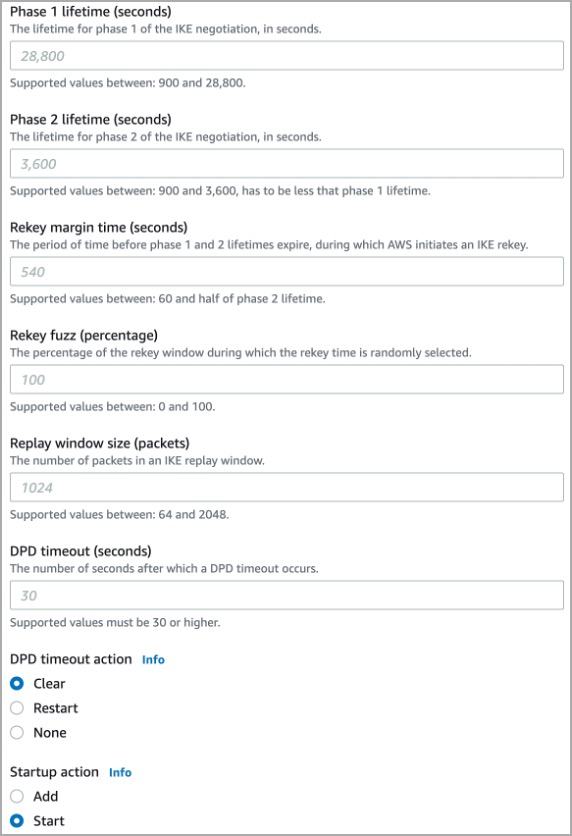
- Click Save Changes.
Update Route Tables
- Navigate to VPC > Virtual private cloud > Route tables.
- Click Add Route.
- Enter 0.0.0.0/0 in the Destination field.
- Select a Virtual Private Gateway from the dropdown list as created in the first section.
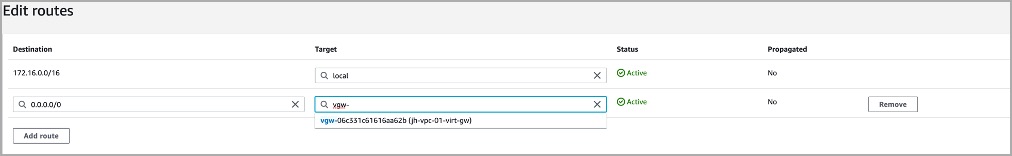
- Click Save Changes.
Configure Umbrella Private Access Tunnel
- Navigate to Deployments > Network Tunnels.
- Click Add.
- Enter the tunnel details.
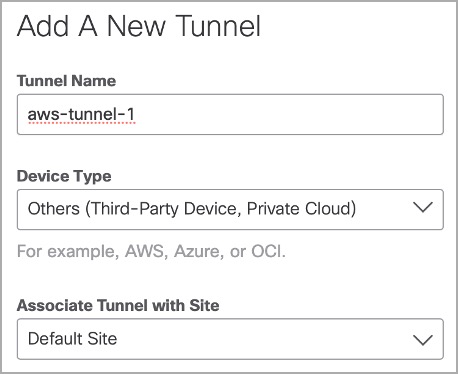
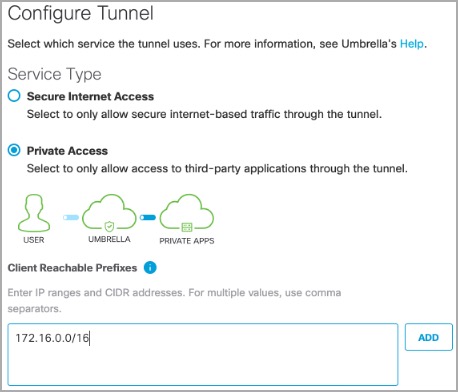
- Select the Service Type. Under Client Reachable Prefixes, enter all public and private address ranges used internally by your organization.
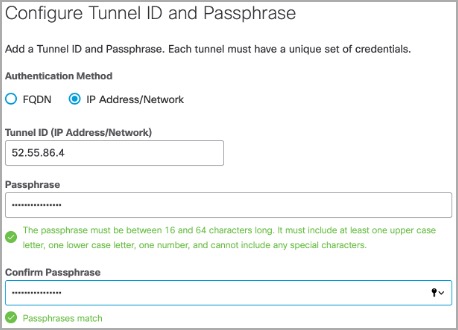
- Select IP Address/Network as the Authentication Method.
- Enter the Passphrase and confirm.
Note: Passphrase is the Pre-shared key copied in step 4. - Click Save.
- Navigate to Deployments > Core Identities > Network Tunnels to verify the tunnel status.

Appendices
-
Azure site to site VPN configuration guide
-
Umbrella Cloud Firewall
https://docs.umbrella.com/deployment-umbrella/v1.0.6/docs/manage-firewall
https://docs.umbrella.com/umbrella-user-guide/docs/supported-ipsec-parameters -
Cisco Cloud Services Router (CSR) 1000V
https://www.cisco.com/c/en/us/td/docs/routers/csr1000/software/azu/b_csr1000config-azure.html
https://www.cisco.com/c/en/us/support/docs/ip/internet-key-exchange-ike/115934-technote-ikev2-00.html
Configure Tunnels with Cisco Router in AWS < Configure Tunnels with AWS Native IPsec > Configure Tunnels with Azure IPsec
Updated over 1 year ago
