Enable Cloud Access Security Broker Features for Microsoft 365 Tenants
Umbrella supports two Cloud Access Security Broker (CASB) features for Microsoft 365:
- Cloud Malware protection for both OneDrive and SharePoint sites within your Microsoft 365 deployment.
Note on running both MS365 and Cloud Malware: MS365 and Cloud Malware both protect users against malware. However, their functionalities are not redundant. MS365 might discover malware that Cloud Malware does not find. Cloud Malware also finds malware that MS365 overlooks. There is value to running MS365 and Cloud Malware simultaneously.
- CASB detection of third-party cloud applications that have been authorized to access a sanctioned Microsoft 365 tenant. You can see information about these third-party applications using the Third-Party Apps Report .
Enable one or both of these features using these instructions.
Table of Contents
Prerequisites
- A minimum user role of Full Admin. For more information, see Manage User Roles.
- Chrome or Firefox (recommended) with pop-up blockers and ad blockers disabled (only for the duration of authorization).
- The user performing the installation must use a service account with a Microsoft 365 Global Admin and active license.
- Audit log must be enabled for Microsoft 365. For more information, refer to Microsoft Technical documentation and search for Turn auditing on or off.
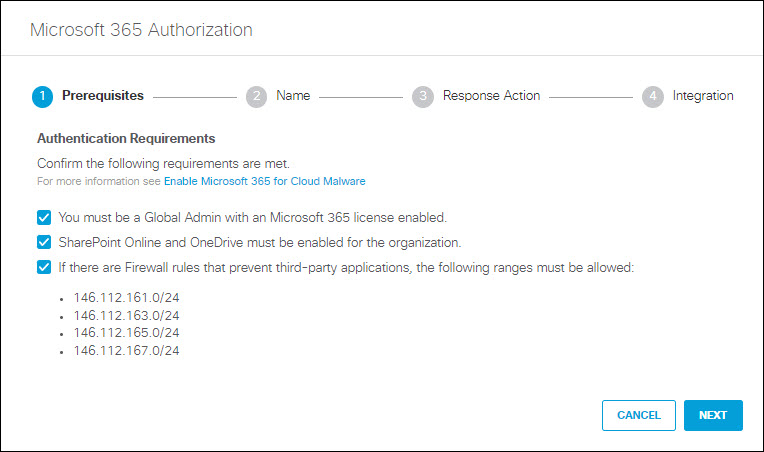
- SharePoint Online and OneDrive must be enabled.
- The following IP addresses must be allowed if there are Firewall rules that prevent third-party applications:
146.112.161.0/24
146.112.163.0/24
146.112.165.0/24
146.112.167.0/24 - If you use Conditional Access Policy (CAP) to restrict access to your Microsoft 365 tenant, you must grant the above Umbrella IP addresses access in the CAP. You must also grant your current egress IP access in the CAP. These IP addresses are cached by Microsoft and used as part of the conditional access checks.
- Users must have the following API permissions for Microsoft:
API/ Permissions Name | Type | Description | Admin Consent Required |
|---|---|---|---|
Microsoft Graph | |||
| Delegated | Access directory as the signed-in user | Yes |
| Application | Read directory data | Yes |
| Delegated | Read all files that user can access | No |
| Application | Read files in all site collections | Yes |
| Delegated | Read items in all site collections | No |
| Delegated | Sign in and read user profile | No |
| Application | Read all users' full profiles | Yes |
Microsoft 365 Management APIs | |||
| Application | Read activity data for the Organization | Yes |
SharePoint | |||
| Application | Full control of all site collections | Yes |
| Application | Read user profiles | Yes |
Limitations
- A tenant that fails to authenticate cannot be deleted.
- Umbrella Cloud Malware attempts to quarantine a file will fail if that file has been locked by Microsoft 365. This may occur if Microsoft 365 Advanced Threat Protection (ATP) has detected malware in the file. In such a case, the lock placed by ATP take precedence over Umbrella's ability to detect or remediate DLP violations in malware.
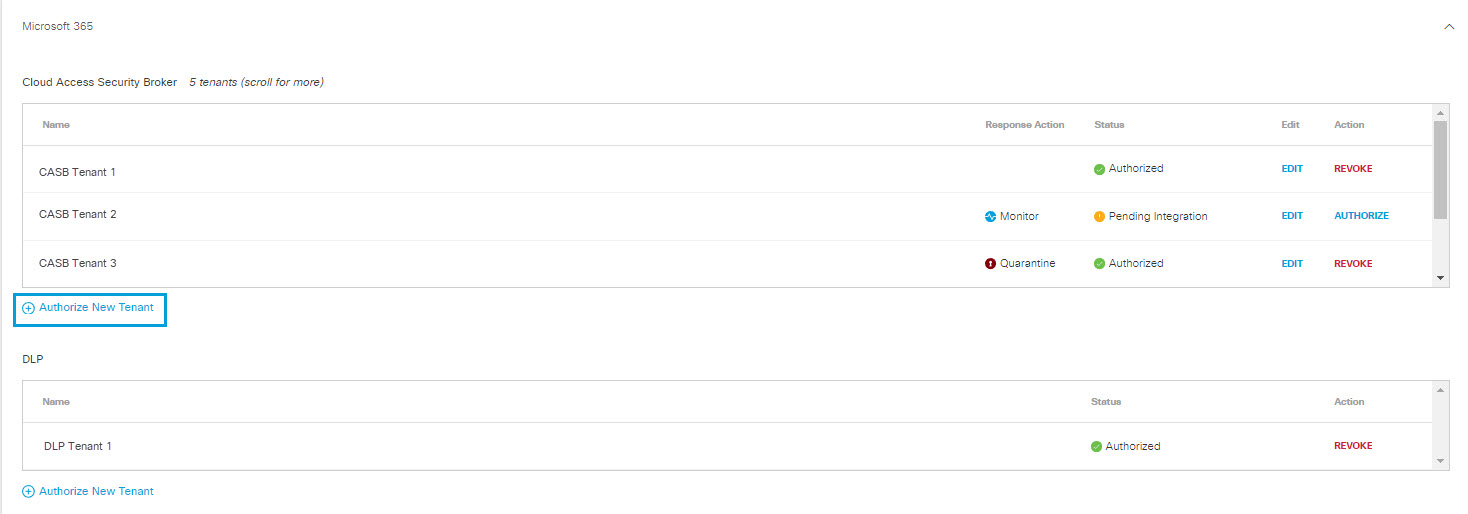
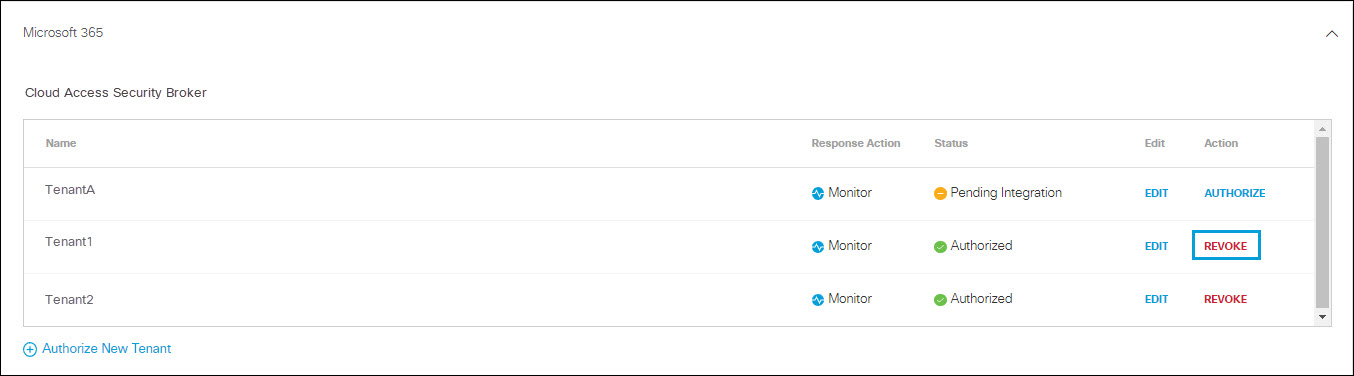
Authorize a Tenant
- Navigate to Admin > Authentication.
- In the Platforms section, click Microsoft 365.
- Click Authorize New Tenant in the Cloud Access Security Broker subsection to add a new Microsoft 365 tenant to your Umbrella environment.
- In the Microsoft 365 Authorization dialog, check the checkboxes to verify you meet the prerequisites and then click Next.
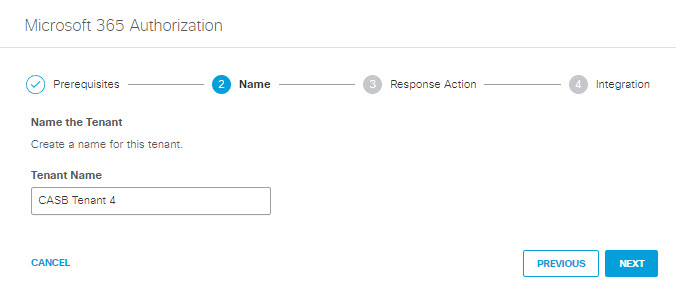
- Add a Tenant Name and then click Next.
- Choose to authorize your Microsoft 365 tenant for Cloud Malware protection, or CASB detection of third-party cloud applications, or both.
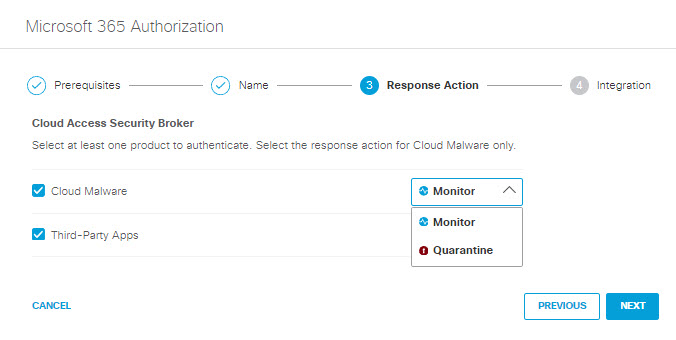
If you choose to authorize for Cloud Malware protection, you must also select a Response Action for Umbrella to apply to Microsoft 365 files found with malware.
- Choose Monitor to cause Umbrella to log files detected with malware. You will be able to manually quarantine these files from the Cloud Malware report.
- Choose Quarantine to:
- Move the file into a folder named Cisco_Quarantine_Malware in the root path of the admin who authorized the tenant, remove all collaborators, and change the file owner to the Microsoft 365 admin.
- Replace the file in its original location with a text file named filename.ppt_Cisco_Quarantined.txt explaining to the original file owner that the file is identified as malware and for more information to contact their organization administrator.
After making your selections, click Next.
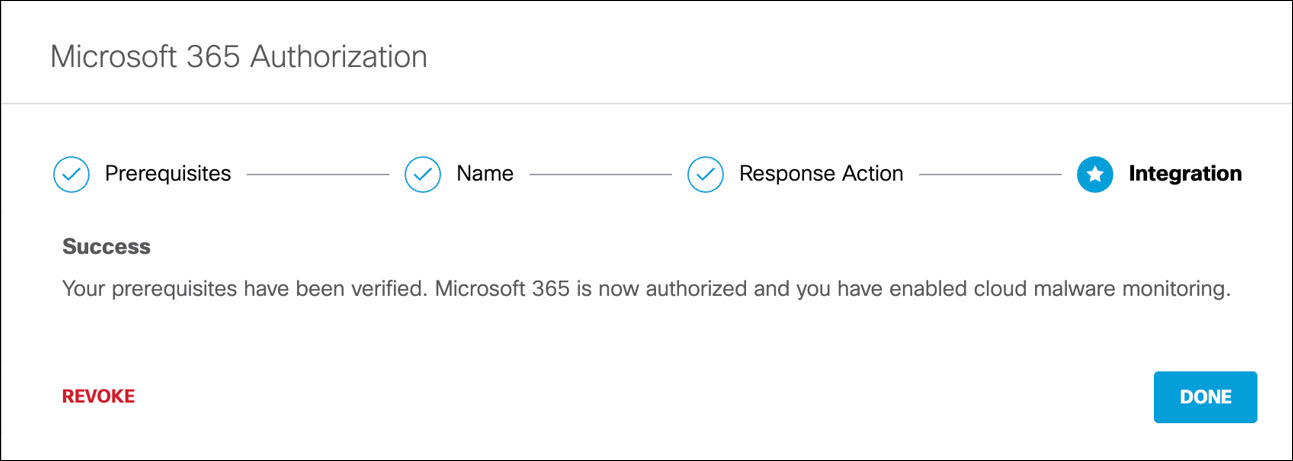
- At the Intgration step, click Next.
You are redirected to the Microsoft 365 login page.
- Log in to Microsoft 365 with admin credentials to grant access.
You are redirected to Umbrella and a message appears showing the integration was successful. It may be up to 24 hours for the integration to be confirmed and appear as Authorized.
- Click Done.
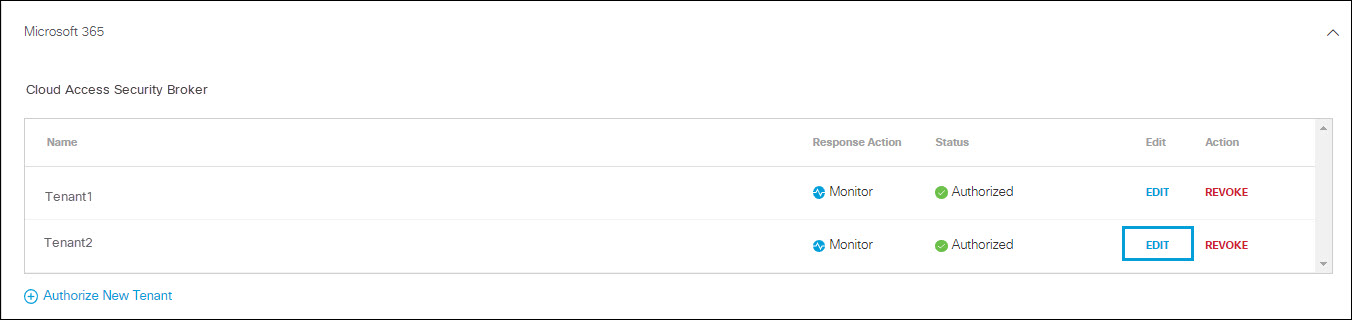
Edit a Tenant
You can change the protection type or Response Action you have selected for a tenant.
- Navigate to Admin > Authentication.
- In the Platforms section, click Microsoft 365.
- In the Cloud Access Security Broker subsection , from the Edit column, click Edit. You can edit any tenant.
-
Choose to authorize your Microsoft 365 tenant for Cloud Malware protection, or CASB detection of third-party cloud applications, or both.
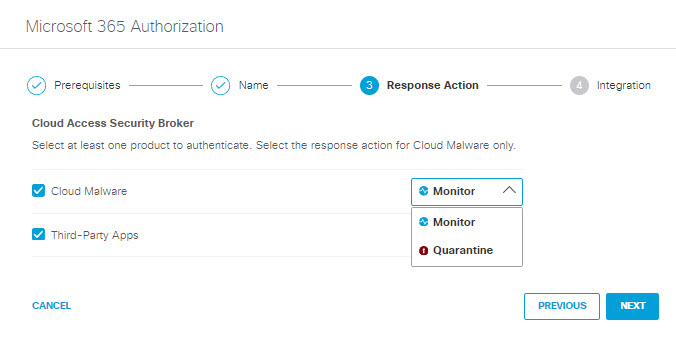
If you choose to authorize for Cloud Malware protection, you must also select a Response Action for Umbrella to apply to Microsoft 365 files found with malware.
- Choose Monitor to cause Umbrella to log files detected with malware. You will be able to manually quarantine these files from the Cloud Malware report.
- Choose Quarantine to:
- Move the file into a folder named Cisco_Quarantine_Malware in the root path of the admin who authorized the tenant, remove all collaborators, and change the file owner to the Microsoft 365 admin.
- Replace the file in its original location with a text file named filename.ppt_Cisco_Quarantined.txt explaining to the original file owner that the file is identified as malware and for more information to contact their organization administrator.
- Click Next.
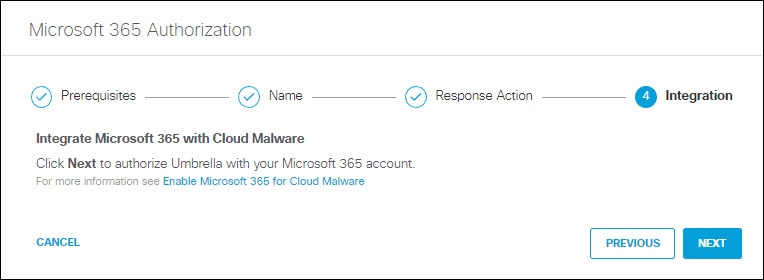
The new Response Action is displayed.
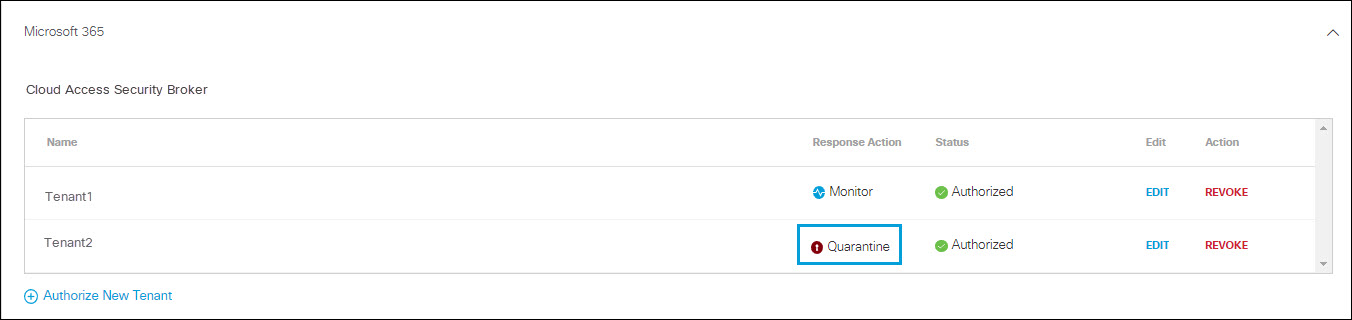
Note: For tenants authorized only for CASB detection of third-party cloud applications, no Response Action is shown.
Revoke Authorization
- For Action, click Revoke. You can revoke any authorized tenant.
- Click Revoke. The selected account is no longer authorized.
Enable Cloud Cloud Access Security Broker Features for Google Drive Tenants < Enable Cloud Access Security Broker Features for Microsoft 365 Tenants > Enable Cloud Malware Protection for ServiceNow Tenants
Updated 13 days ago